Introduction
The intent of this article is to thoroughly examine the practicality and implications of using private endpoints exclusively in Azure for enhanced security. By exploring the feasibility of this approach, we aim to understand its realistic application, potential limitations, and overall effectiveness. This article will discuss the necessity of public endpoints in some Azure services and provide a detailed comparison between private endpoints, service endpoints, and private links. Furthermore, it will delve into the implementation of private endpoints and the role of DNS in resolving these endpoints.
Understanding Private Endpoints and Their Importance
What are Private Endpoints?
Private endpoints are network interfaces that connect you privately and securely to a service powered by Azure Private Link. Private endpoints utilize a private IP address from your VNet, effectively bringing the service into your VNet. This ensures that traffic between your VNet and the service travels only through the Azure Backbone Network, avoiding exposure to the public internet.
Benefits of Private Endpoints
- Enhanced Security: By keeping traffic within the private network, private endpoints significantly reduce the risk of data exposure.
- Compliance: Private endpoints help in meeting regulatory requirements by keeping data within trusted boundaries.
- Improved Performance: Reduced latency as traffic remains within the Azure Backbone Network.
Service Endpoints vs. Private Links Vs. Private Endpoints
Service Endpoints
Service endpoints extend your VNet identity to the Azure service over a direct connection without the need for public IP addresses. They allow Azure services to access your VNet directly, providing secure and fast connectivity.
Example
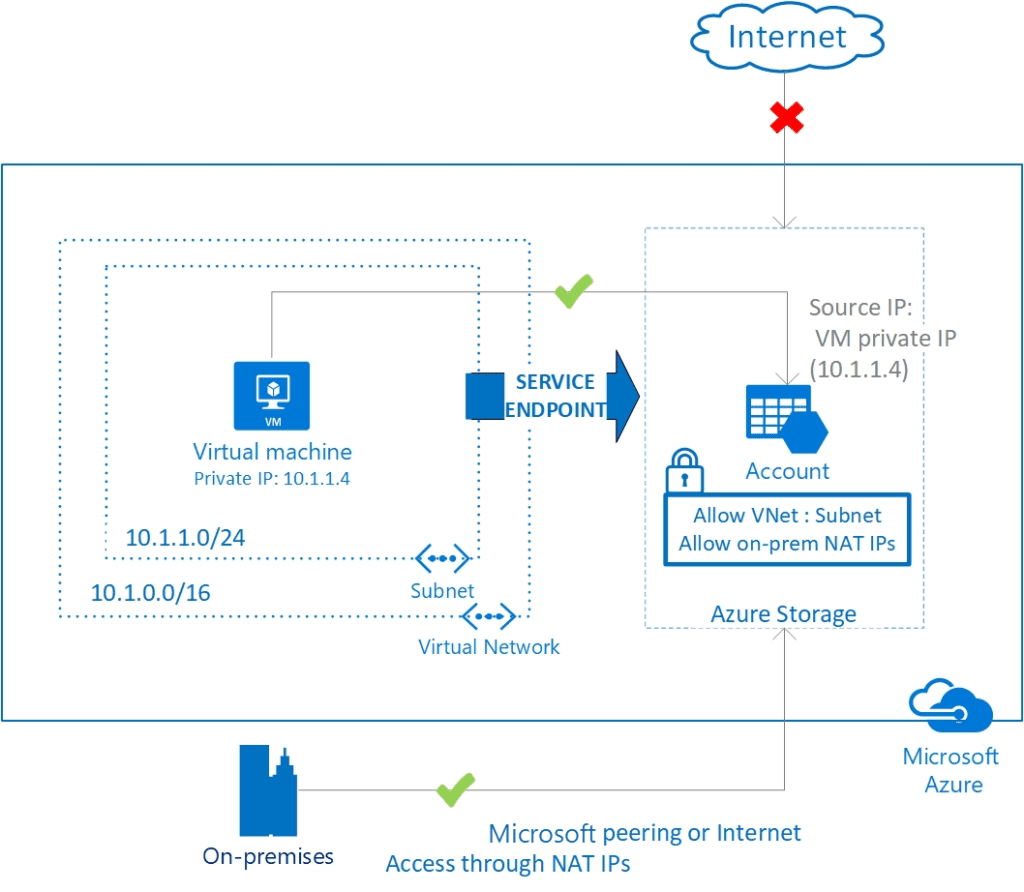
Consider an Azure Storage account. In the provided graphic, we see a virtual machine (VM) connected to this storage account using service endpoints. By enabling service endpoints, you can allow traffic only from your virtual network (VNet) to access the storage account. This setup ensures that the data remains secure while maintaining high performance. The service endpoints provide a direct and secure connection over the Azure backbone network, bypassing the public internet and reducing exposure to potential threats.
Private Links
Private Links enable private connectivity to Azure services via private endpoints in your VNet. They provide a secure connection to Azure services within the VNet, utilizing private IP addresses.
Example
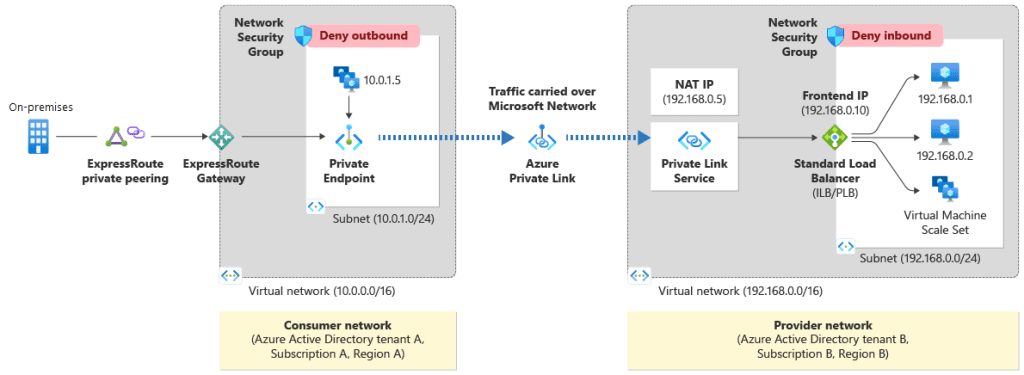
Consider a scenario where you have a Virtual Machine Scale Set (VMSS) with a Network Security Group (NSG) in your virtual network (VNet). In the provided graphic, we see the following components:
VM Scale Set with NSG: The VMSS is protected by an NSG, which has a rule to deny outbound traffic to the private endpoint with IP address 10.0.1.5. This rule ensures that only specific traffic is allowed to reach the private endpoint, enhancing security by preventing unauthorized outbound connections.
ExpressRoute Private Peering: This setup includes ExpressRoute private peering, which provides a private connection between your on-premises network and Azure, bypassing the public internet.
Traffic Carried Over Microsoft Network: The traffic from the VMSS is carried over the Microsoft backbone network to ensure secure and reliable connectivity.
Private Link Service: The traffic reaches the Private Link service, which is configured to provide private connectivity to your service.
NSG on Provider Network: On the provider’s side, another NSG is in place to control traffic to the Private Link service. This NSG has a rule to deny inbound traffic to the frontend IP and the standard load balancer. This rule ensures that only traffic from the private endpoint is allowed, preventing unauthorized access from other sources.
By creating a private link, you can connect to the Private Link service through a private endpoint, ensuring that the traffic flows securely within the VNet and over the Microsoft backbone network. This setup provides secure and private connectivity, reducing exposure to potential threats and maintaining high performance.
Private Endpoints
Private endpoints are recommended when you need to bring a PaaS service or an IaaS resource into your VNet. They provide the highest level of security by avoiding public IPs altogether. For example, you can use private endpoints to securely connect to an Azure Storage account (PaaS) or a virtual machine (IaaS) within your VNet, ensuring that the traffic flows securely within the Azure backbone network and does not traverse the public internet.
Example
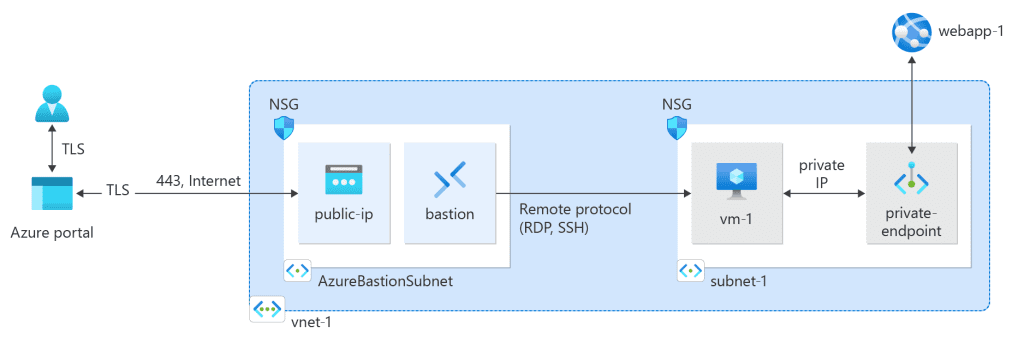
Consider the following scenario: You have a Virtual Machine (VM) with a Network Security Group (NSG) in your virtual network (VNet). In the provided graphic, we see the following components:
Public IP and Bastion: On the left side, there is an NSG with a public IP and a Bastion service. This public IP is for the Bastion host, which is located in the AzureBastionSubnet. The Bastion service allows secure and seamless RDP and SSH connectivity to the VM without exposing it to the public internet.
VM 1 with Private IP: On the right side, there is a VM (VM 1) with a private IP address. This VM is using a private endpoint to connect to a web application (WebApp 1). The private endpoint ensures that the traffic flows securely within the VNet.
Private Endpoint for WebApp 1: The private endpoint is used to connect to WebApp 1, ensuring that the traffic remains within the Azure backbone network and does not traverse the public internet.
By creating a private link, you can connect to WebApp 1 through a private endpoint, ensuring that the traffic flows securely within the VNet and over the Microsoft backbone network. This setup provides secure and private connectivity, reducing exposure to potential threats and maintaining high performance.
Implementing Private Endpoints
Steps for Implementation
- Create a Private Link Service: Define the service you want to expose via Private Link.
- Create a Private Endpoint: Establish a private endpoint in the desired VNet.
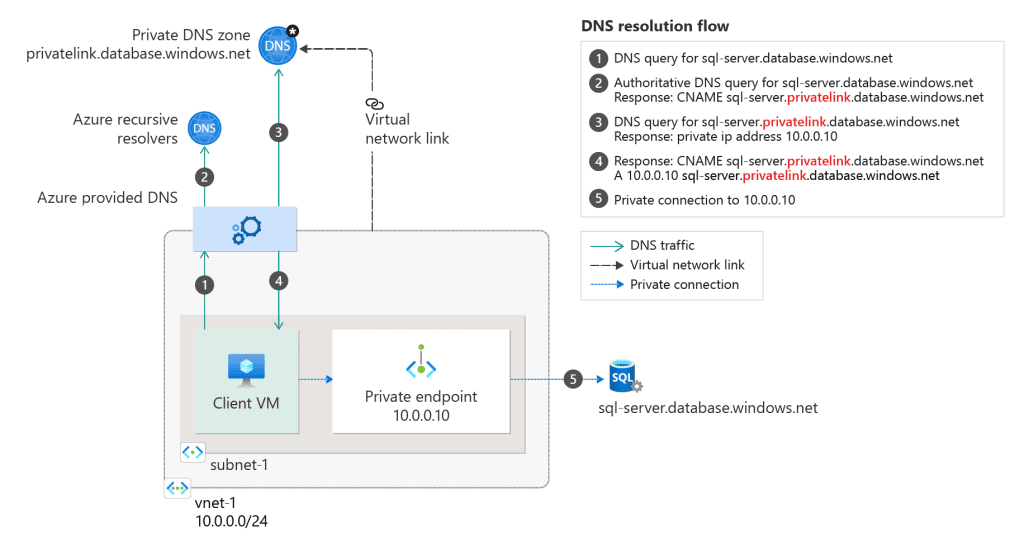
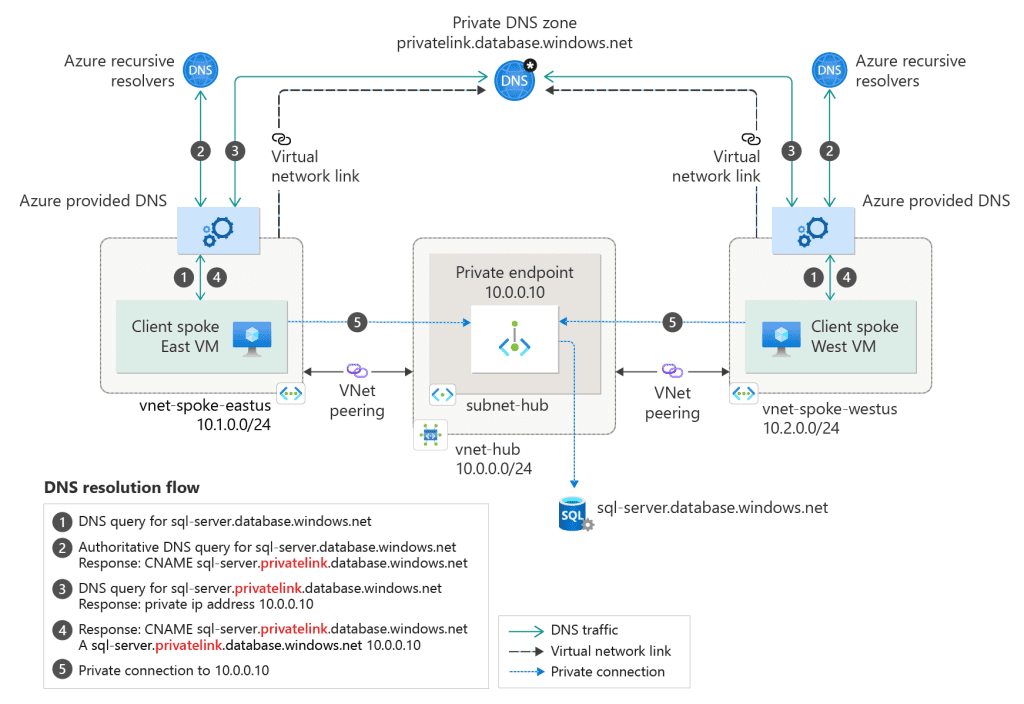
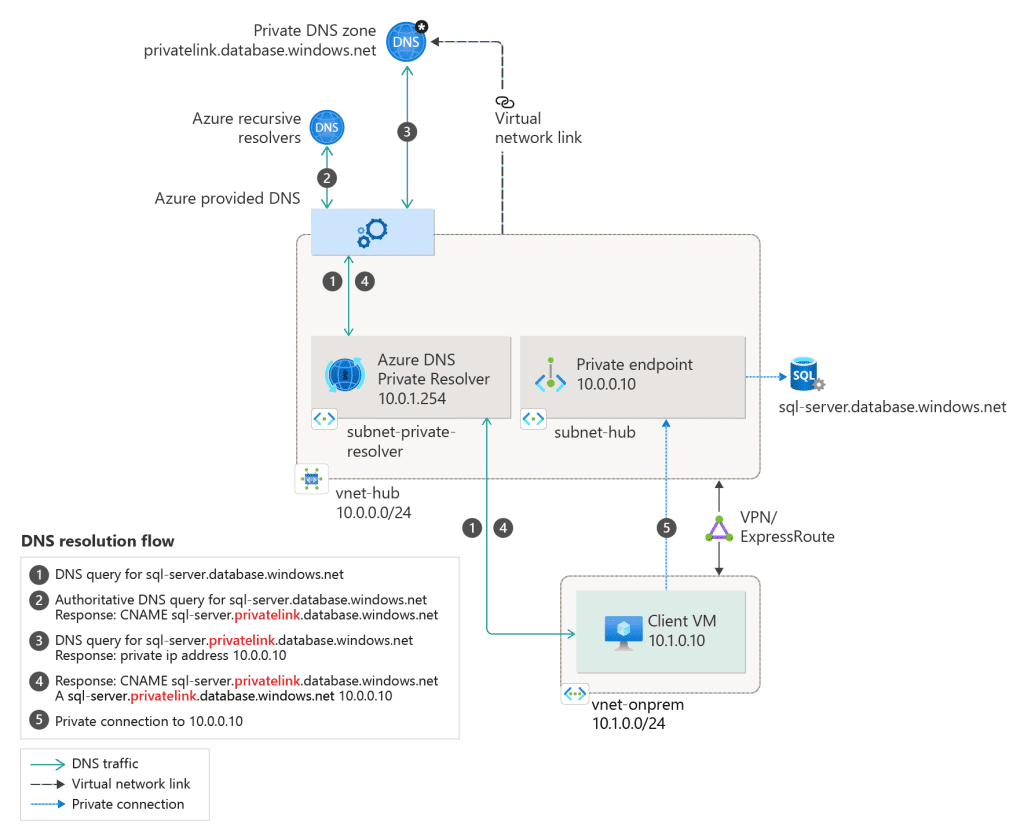
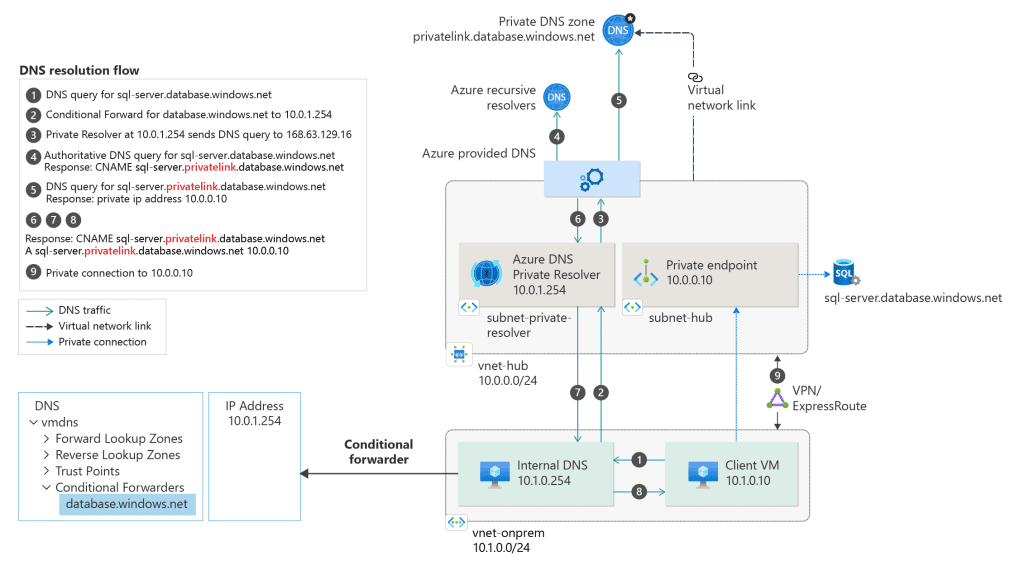
- Configure DNS: Ensure proper DNS resolution for the private endpoint.
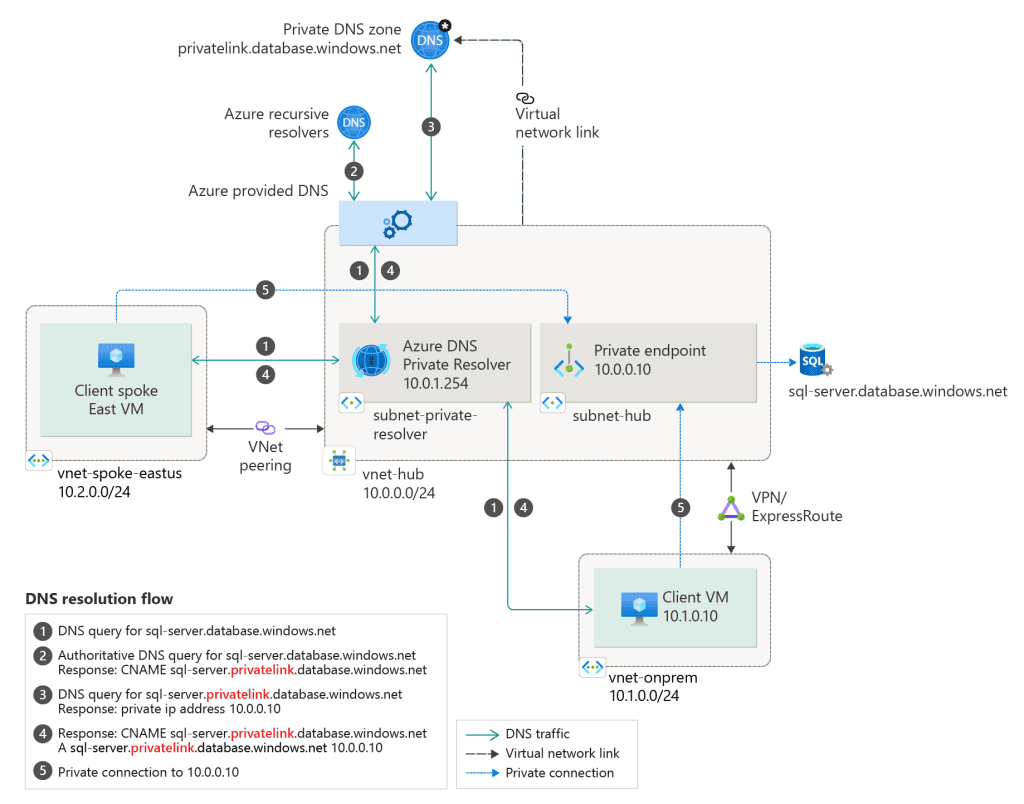
DNS and Private Endpoints
Private endpoints require DNS to resolve the private IP addresses. Organizations can use Azure DNS private zones or their own DNS servers to manage this resolution, ensuring seamless connectivity.
Azure DNS Private Zones vs. Own DNS Services
- Azure DNS Private Zones: Recommended for most scenarios. They provide easy integration with Azure services, automatic DNS record management, and global availability.
- Own DNS Services: Suitable for organizations with specific compliance or operational requirements that necessitate using their DNS infrastructure.
Benefits of Azure DNS Private Zones
- Seamless Integration: Simplifies DNS management within Azure environments.
- Automatic Management: Automatically manages DNS records for private endpoints.
- Global Availability: Ensures high availability and performance with a global DNS network.
Limitations and Considerations
Services Requiring Public Endpoints
Certain Azure services, such as Azure Firewall Premium and Azure Front Door, require public endpoints. These services are designed with built-in security features like DDoS protection to mitigate risk. Other services requiring public endpoints include:
- Azure Content Delivery Network (CDN): Provides fast content delivery with robust security features.
- Azure Traffic Manager: Distributes traffic across multiple regions for high availability and performance.
- Azure Application Gateway: Offers advanced load balancing and security features, including Web Application Firewall (WAF).
Security of Services with Public Endpoints
Even though some services require public IPs, they are equipped with advanced security measures. For instance:
- Azure Firewall: Provides network and application-level protection with built-in high availability and scalability.
- Azure Front Door: Offers global load balancing and enhanced security with Web Application Firewall (WAF) and SSL/TLS termination.
- Azure CDN: Delivers content securely and efficiently with DDoS protection and SSL/TLS encryption.
Central Firewall and Connectivity Subscription
Following the Cloud Adoption Framework, utilizing a central firewall in a connectivity subscription enhances security by acting as a control point for traffic between VNets and the internet. The central firewall helps manage and protect traffic flow, ensuring secure communication across the entire Azure environment.
Recommended Usage
It is recommended to use the central firewall in conjunction with publicly exposed services like Azure Front Door and Azure Application Gateway. This setup allows you to leverage the security features of these services while maintaining control over traffic flow and ensuring that only authorized traffic can access your resources.
Benefits of a Central Firewall
- Unified Security Management: Centralizes security policies and monitoring.
- Enhanced Control: Manages traffic flow between VNets and the internet effectively.
- Scalability: Scales security measures as your Azure environment grows.
Microsoft Sentinel and Its Role
Microsoft Sentinel is a cloud-native security information and event management (SIEM) system that provides intelligent security analytics and threat intelligence. By integrating with a central firewall, Sentinel enhances security monitoring and threat detection capabilities.
- Advanced Threat Detection: Uses built-in AI and machine learning to identify security threats.
- Comprehensive Visibility: Provides insights into security events and logs across your Azure environment.
- Scalable Response: Enables automated response to security incidents, improving overall security posture.
However, it is crucial to note that while Sentinel offers sophisticated tools and insights, it requires skilled personnel to interpret findings and take necessary actions. The AI capabilities in Sentinel help understand security-relevant findings and offer recommendations to enhance security posture.
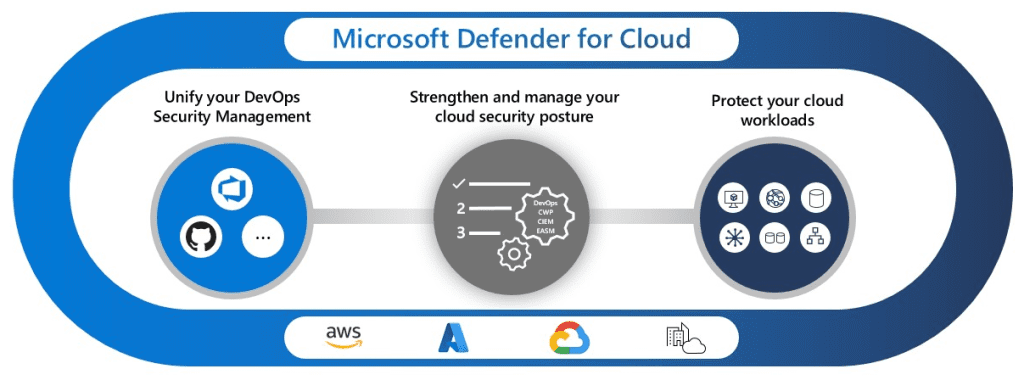
Defender for Cloud vs. Sentinel
Microsoft Defender for Cloud (previously known as Azure Security Center) and Microsoft Sentinel serve different purposes but complement each other in a comprehensive security strategy.
Microsoft Defender for Cloud provides built-in security management and threat protection for Azure services, as well as other cloud platforms and on-premises environments. It offers recommendations and compliance assessments to improve security posture.
Microsoft Sentinel focuses on SIEM capabilities, providing advanced threat detection, incident response, and continuous monitoring across the entire Azure environment. It also supports integration with other cloud platforms and on-premises environments through various connectors.
Organizations not ready to adopt Sentinel can start with Defender for Cloud to enhance their security posture. As they grow and require more advanced threat detection and response capabilities, they can integrate Sentinel into their security strategy.
Conclusion
Using private endpoints in Azure is a highly effective approach to enhancing security by avoiding exposure to the public internet. However, it is important to acknowledge that some Azure services necessitate public endpoints due to their design and functionality. These services are built with robust security features to mitigate risks. By understanding the differences between private endpoints, service endpoints, and private links, and by implementing appropriate DNS configurations, organizations can achieve a secure and efficient Azure environment. Adopting a central firewall in a connectivity subscription further strengthens the security posture, aligning with best practices outlined in the Cloud Adoption Framework. Additionally, integrating Microsoft Sentinel with a central firewall and other services enhances threat detection and response capabilities, while Microsoft Defender for Cloud provides essential security management and protection.