Introduction
Introduction: In today’s hybrid cloud environments, effectively managing network address space is crucial for ensuring seamless connectivity and scalability. This article provides best practices and recommendations for allocating network address ranges in Azure and on-premises datacenters, based on the Cloud Adoption Framework, the Well-Architected Framework, and other relevant sources.
Network Setup: Connectivity Subscription and Individual Spokes
Understanding the network setup is essential for designing a scalable and efficient architecture. This section delves into the hub-and-spoke topology, connectivity subscription, and individual spokes.
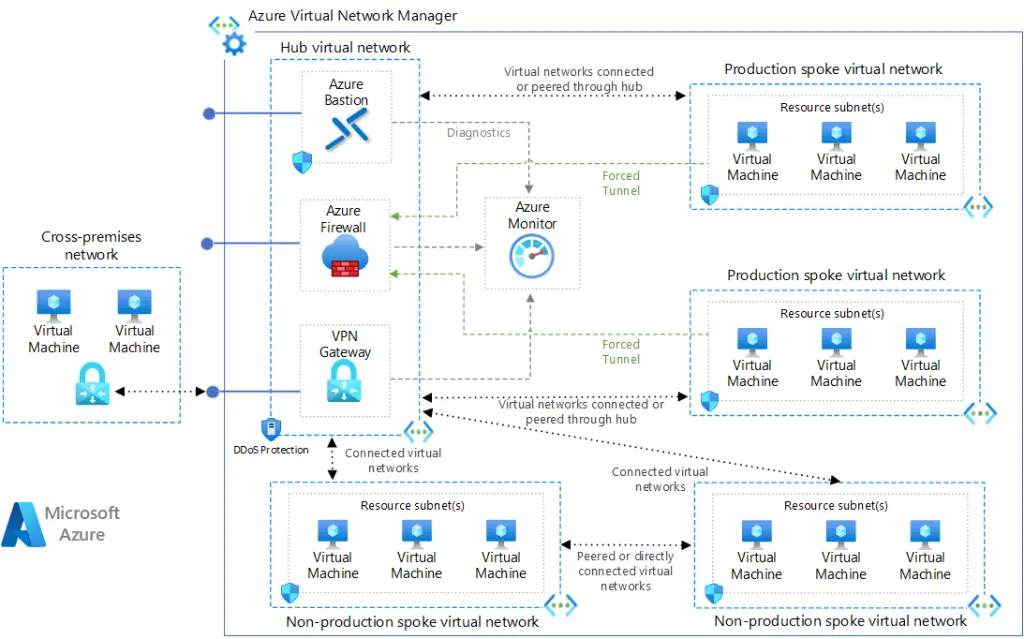
Hub-and-Spoke Topology
The hub-and-spoke network topology is a common architecture in Azure. The hub is a central VNet that acts as a connectivity point to on-premises networks and other Azure VNets. The spokes are VNets that peer with the hub and can be used to isolate workloads.
Connectivity Subscription
The connectivity subscription hosts the hub VNet, which includes shared services such as VPN gateways, ExpressRoute gateways, and Azure Firewall. This subscription is managed centrally to ensure consistent network policies and security controls.
Individual Spokes
Each spoke VNet is deployed in separate subscriptions, known as application landing zone subscriptions. These spokes are peered with the hub VNet to allow communication between resources in different VNets while maintaining isolation.
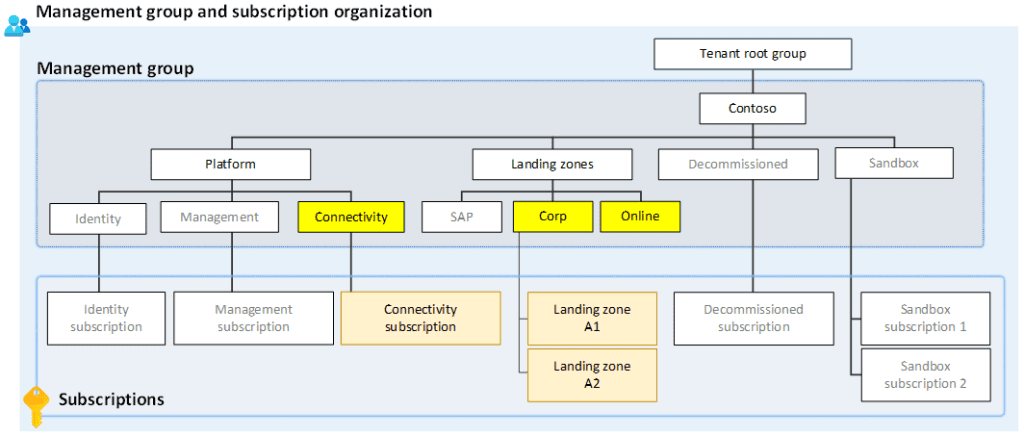
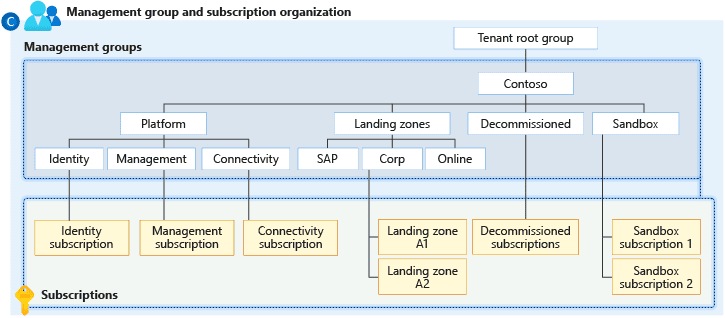
Management Groups and Subscriptions
Properly structuring management groups and subscriptions is crucial for maintaining control and governance. This section explains their roles in organizing and managing resources within an enterprise.
Corp Management Group and Subscriptions
The corp management group is used to manage corporate resources and subscriptions. It includes policies and access controls that apply to all subscriptions under this group.
Online Management Group and Subscriptions
The online management group is used to manage online services and applications. Similar to the corp management group, it includes policies and access controls for all subscriptions under this group.
VPN Gateway or ExpressRoute Gateway in Connectivity Subscription
Gateways play a vital role in establishing secure and reliable cross-premises connectivity. This section discusses the use of VPN and ExpressRoute gateways in the connectivity subscription.
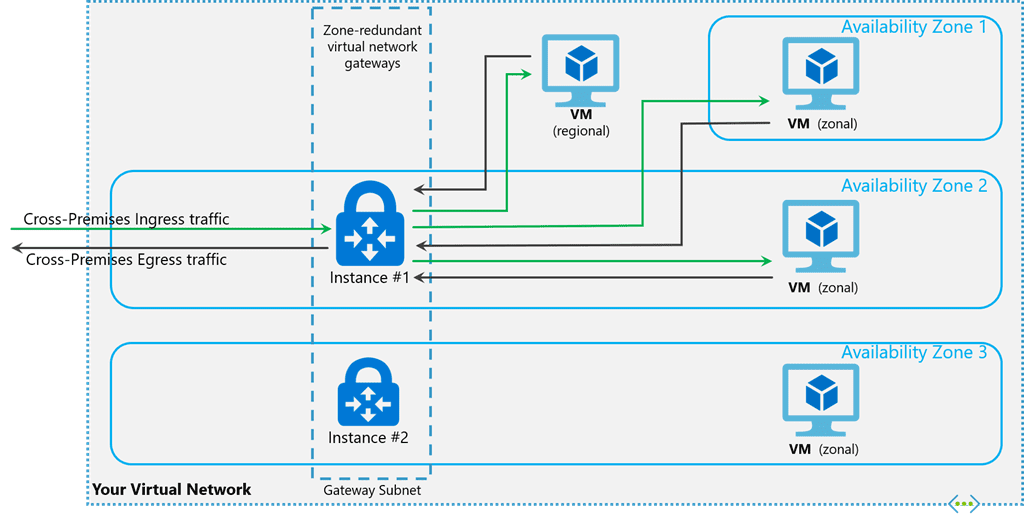
VPN Gateway
A VPN gateway is used to establish secure cross-premises connectivity between the on-premises network and Azure VNets. It supports site-to-site (S2S), point-to-site (P2S), and VNet-to-VNet connections. NAT is supported on VPN gateways with SKUs VpnGw2 to VpnGw5 and VpnGw2AZ to VpnGw5AZ.
ExpressRoute Gateway
An ExpressRoute gateway provides a dedicated, private connection between the on-premises network and Azure. It offers higher bandwidth and lower latency compared to VPN gateways. NAT is also supported on ExpressRoute gateways for public and Microsoft peering.
Address Space Allocation
Proper address space allocation is critical for avoiding conflicts and ensuring future scalability. This section provides guidance on planning and managing address space allocation.
Planning Address Space
Allocate address space with future growth in mind. Ensure that the address ranges do not overlap between on-premises and Azure environments.
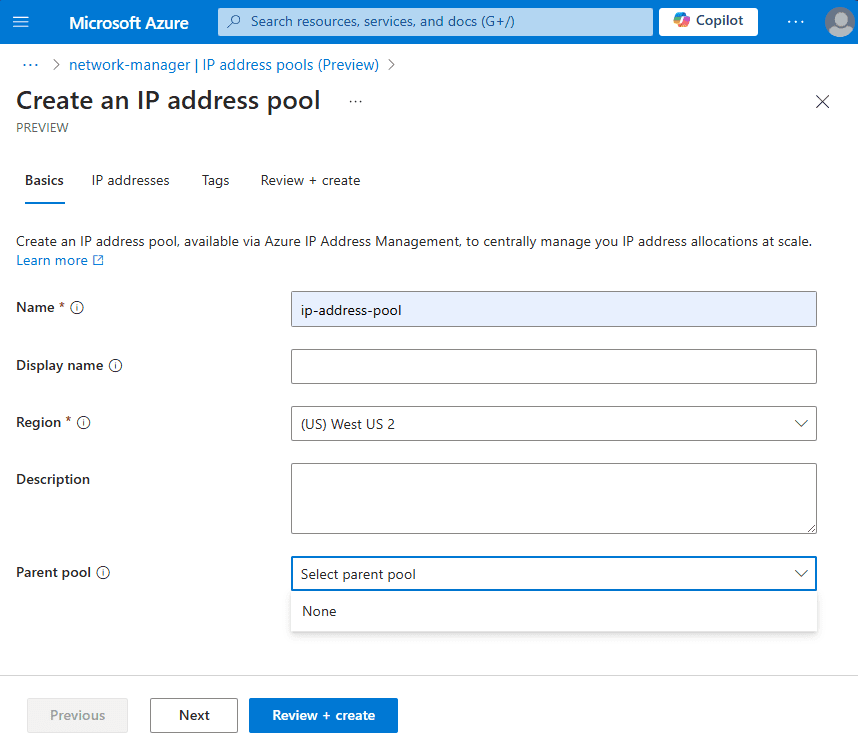
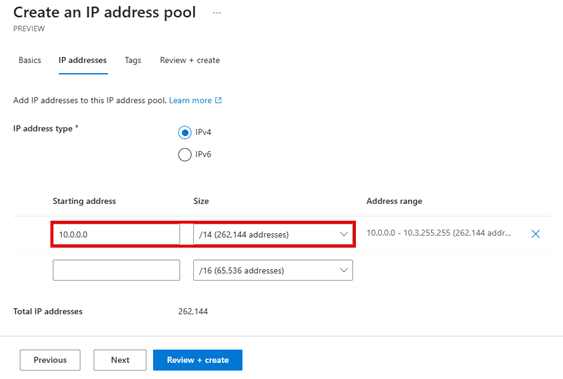
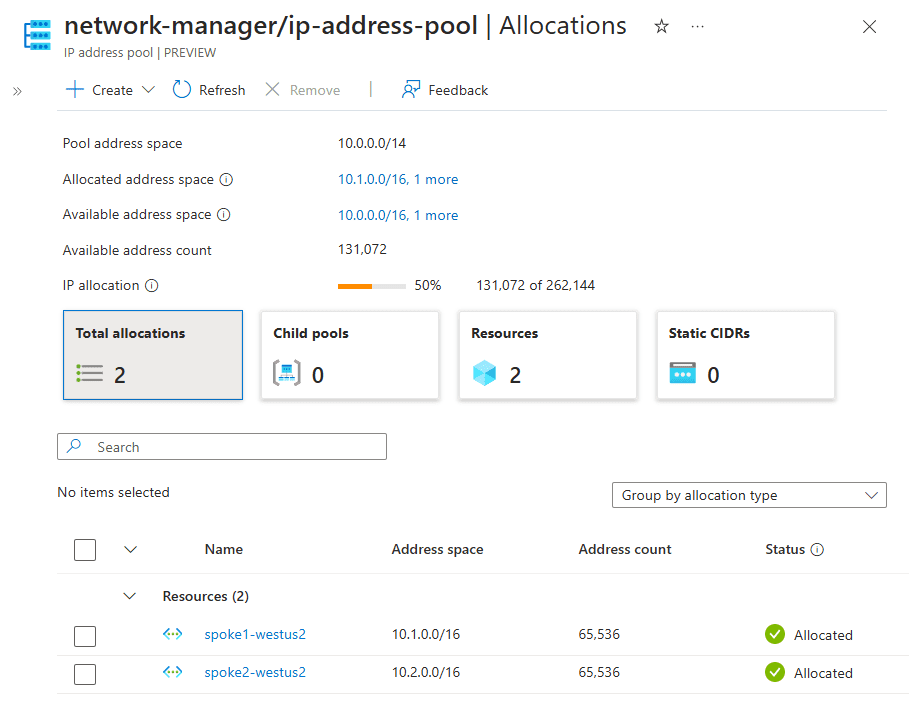
Tools for Address Space Management
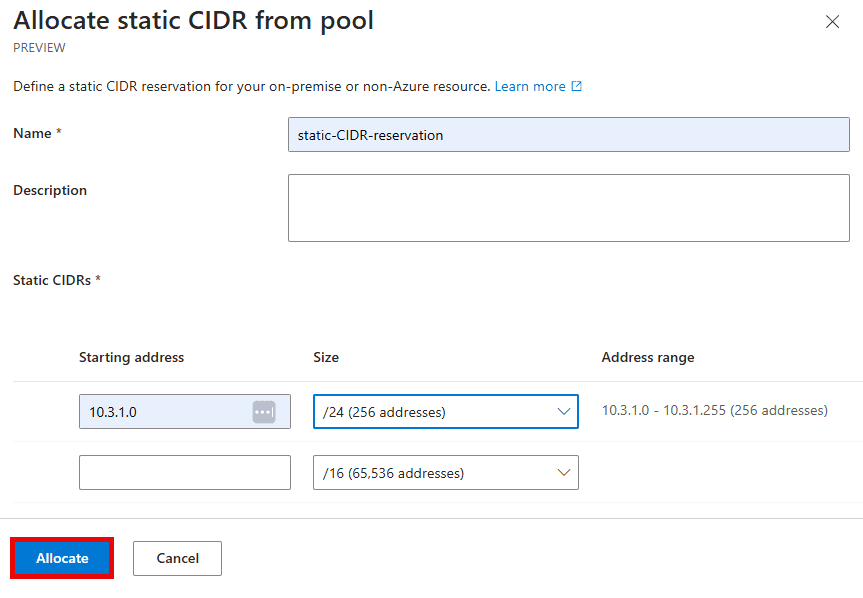
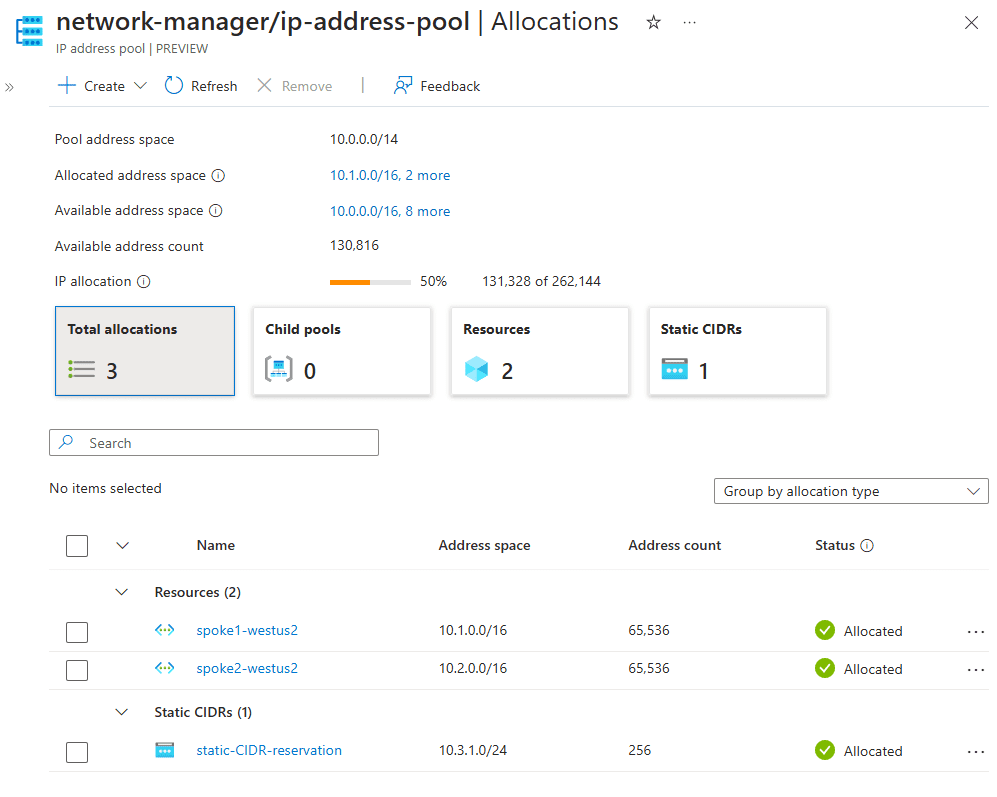
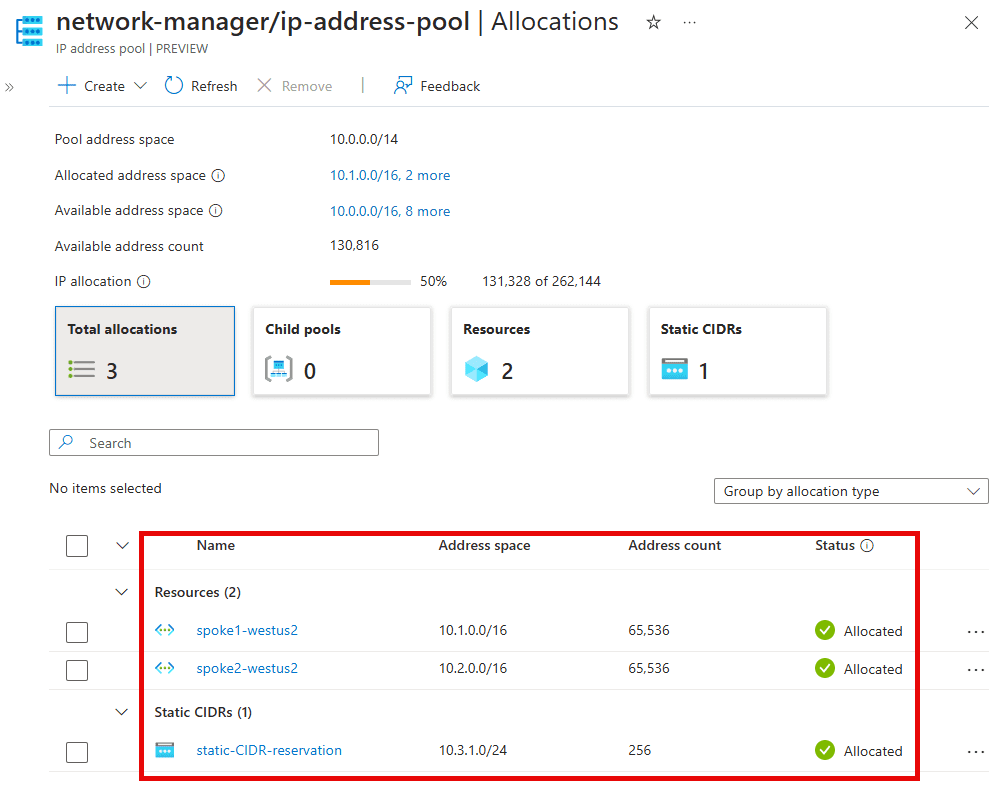
Azure provides tools such as IP Address Manager (IPAM) and Azure Virtual Network Manager (AVNM) to help manage address space allocation efficiently.
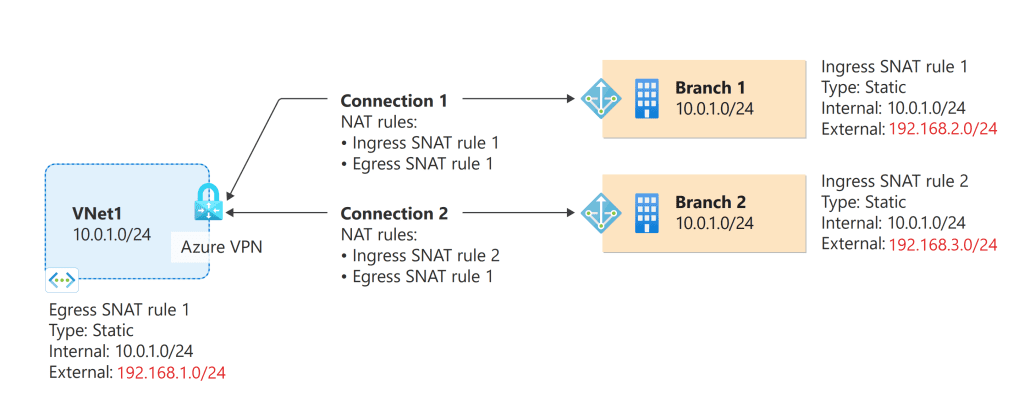
Network Address Translation (NAT)
NAT can be used to conserve IP addresses by mapping an external IP address and port to a larger set of internal IP addresses. This is particularly useful when there is a shortage of address space. NAT is supported on premium VPN gateways (VpnGw2 to VpnGw5 and VpnGw2AZ to VpnGw5AZ) and ExpressRoute gateways.
Considering IPv6
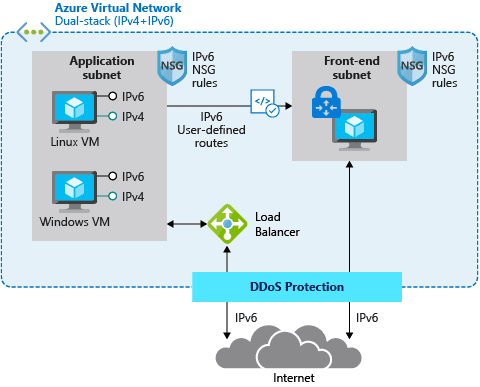
Given the scarcity of IPv4 addresses, consider adopting IPv6. IPv6 provides a vastly larger address space and can coexist with IPv4, allowing for a phased transition. Implementing IPv6 where needed can help future-proof the network and provide connectivity to IPv6-only clients.
Deploying Gateways for Connectivity
Ensuring high availability and redundancy is essential for reliable connectivity. This section explains the deployment of gateways, including both active-active and active-passive configurations.
On-Premises and Cloud Gateways
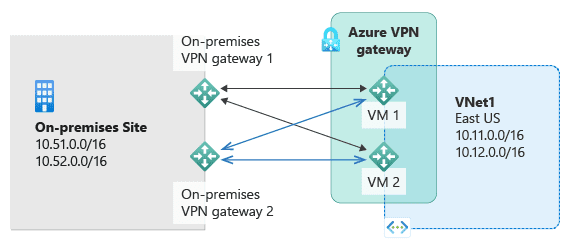
To establish connectivity, you will need to deploy one gateway on-premises and one in the cloud. If considering an active-active setup, this would result in a total of four gateways: two in the cloud and two on-premises. This setup ensures high availability and redundancy.
Active-Active Configuration
In an active-active configuration, both gateways in the cloud and on-premises are active simultaneously, providing load balancing and failover capabilities. This setup requires two local network gateways and two connections for each on-premises VPN device.
Active-Passive Configuration
In an active-passive setup, one gateway is active while the other is on standby. If the active gateway fails, the passive gateway takes over, ensuring continuity of service. This setup typically involves one VPN gateway and two local network gateways.
Multiple Hubs in Different Regions
For organizations with operations in multiple regions, having multiple hubs is a common practice. This section discusses the use of multiple hubs and the Virtual WAN (VWAN) setup.
Regional Hubs
A hub resides within a single region. If a customer has major operations in multiple regions, such as West Europe and West US, they would likely have separate hubs in each region. This setup ensures regional redundancy and optimized performance.
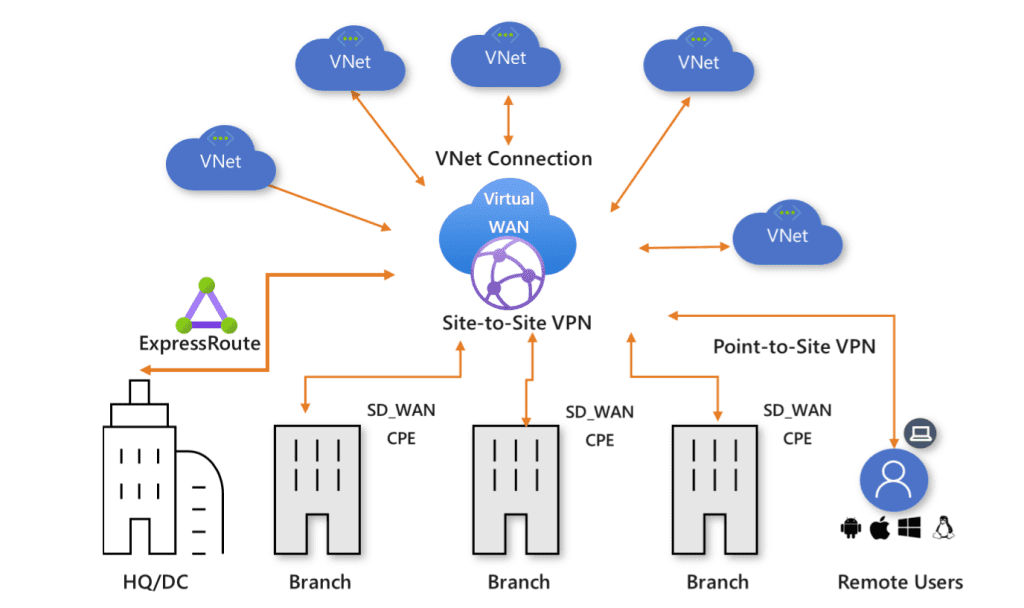
Virtual WAN (VWAN) Setup
For a more scalable solution across multiple regions, consider using Azure Virtual WAN (VWAN). VWAN provides a unified and global network backbone, allowing seamless connectivity between regions. It simplifies network management and enhances security by centralizing network policies and controls.
Non-Peered Subscriptions and Address Space
Understanding the considerations for non-peered subscriptions and address space is important for avoiding conflicts and ensuring efficient network management.
Non-Overlapping Address Spaces
Non-peered subscriptions, especially those in the online management group, may not require non-overlapping address spaces since they are not peered with the connectivity hub.
Key Considerations for Network Design
Creating a robust and efficient network architecture involves adhering to fundamental principles. This section highlights key considerations for network design, including security, cost-efficiency, scalability, simplicity, and high availability.
Security:
- Ensure that the network design adheres to security best practices, including the use of NSGs, Azure Firewall, and other security measures.
Cost-Efficiency:
- Optimize the network design to minimize costs while maintaining performance and security.
Scalability:
- Design the network to be scalable, allowing for easy expansion as the organization’s needs grow.
Simplicity:
- Keep the network design as simple as possible to reduce complexity and ease management.
High Availability:
- Ensure high availability by implementing redundancy and failover mechanisms.
Additional Recommendations
Optimizing network performance and management requires following best practices from various sources. This section provides additional recommendations based on insights from Azure Advisor, the Well-Architected Framework, and other sources.
Use Azure Advisor:
- Azure Advisor provides recommendations for optimizing performance, security, and cost. Regularly review and implement these recommendations to maintain an efficient and secure network.
Implement Redundancy:
- Apply redundancy at different levels, including compute, data, and network tiers, to ensure reliability and high availability.
Monitor and Optimize Performance:
- Continuously monitor network performance using Azure Network Watcher and other monitoring tools. Optimize network configurations based on performance metrics and usage patterns.
Leverage Azure Well-Architected Framework:
- Follow the principles of the Azure Well-Architected Framework to ensure that your network design aligns with best practices for reliability, security, cost optimization, operational excellence, and performance efficiency.
Conclusion
By following these best practices and recommendations, organizations can effectively manage their network address space, ensuring seamless connectivity and scalability in hybrid cloud environments. Utilizing tools like IPAM and AVNM, considering options like NAT and IPv6, and adhering to the principles of the Cloud Adoption Framework and the Well-Architected Framework can further enhance address space management.