Introduction
In this article, we aim to provide Solution Architects and IT Managers with comprehensive guidance on managing the upcoming retirement of Basic SKU Public IPs. The current challenge is the need to migrate from Basic to Standard SKU to avoid service disruptions. We will explore key concepts, differences between gateway types, and provide actionable steps to ensure minimal downtime during the upgrade process. This article will cover fundamental concepts necessary to understand the implications of the Basic SKU retirement and the upgrade processes for ExpressRoute and VPN Gateways. We will explain the differences between various SKUs, gateway types, and redundancy options to provide a solid foundation for the detailed guidance that follows.
Key Concepts
Understanding the key concepts is crucial for comprehending the impact of the Basic SKU retirement for Public IPs. This section will cover the differences between Basic and Standard SKUs, gateway types, and redundancy options.
Basic vs. Standard SKU for Public IPs
The Basic SKU for Public IPs is being retired by 30 September 2025, necessitating a migration to the Standard SKU. The Standard SKU offers enhanced features such as zone redundancy, improved security, and higher availability. Understanding these differences is crucial for planning the upgrade process. The Basic SKU provides a single point of failure, whereas the Standard SKU offers zone redundancy, which distributes the public IP across multiple fault zones, ensuring higher availability and resiliency.
VPN Gateway vs. ExpressRoute Gateway
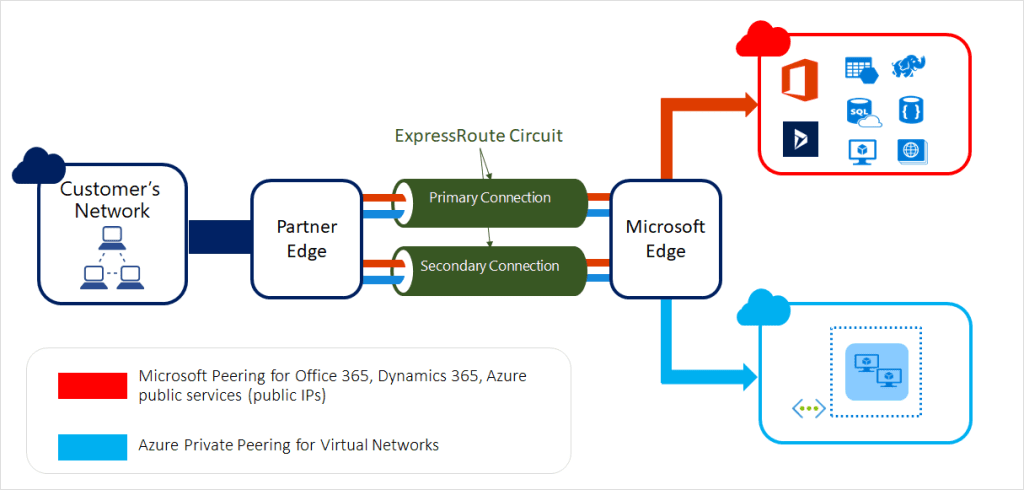
VPN Gateway and ExpressRoute Gateway serve similar purposes but differ in their offerings. ExpressRoute is a premium service providing dedicated private connections, while VPN Gateway uses encrypted tunnels over the internet. ExpressRoute offers higher reliability, lower latency, and higher bandwidth compared to VPN Gateway. Knowing these differences helps in choosing the right upgrade path and understanding the implications of each option.
Local Gateway vs. Cloud Gateway
Local gateways are on-premises devices that connect to cloud gateways in Azure. Cloud gateways manage the connection to Azure services. Differentiating between these gateways is important for configuring and maintaining connectivity during upgrades. Local gateways require manual configuration updates when public IPs change, whereas cloud gateways can be managed and updated through the Azure portal.
Dual Connectivity
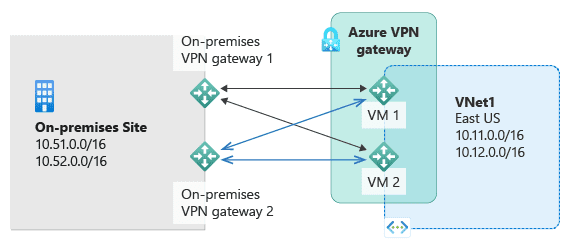
Dual connectivity involves using multiple gateways for redundancy. This setup ensures continuous connectivity even if one gateway fails. Understanding dual connectivity helps in planning resilient network architectures. Dual connectivity can be achieved by deploying multiple VPN or ExpressRoute gateways, providing failover capabilities and ensuring high availability. There are two main options for dual connectivity: active-active and active-passive.
Active-Active Setup
In an active-active setup, multiple gateways are simultaneously active and operational. This configuration ensures that if one gateway fails, the other gateways can seamlessly pick up the workload, preventing disruptions in service. Active-active setups offer high scalability, parallel processing, and fault tolerance. However, they can be complex to configure and may incur higher costs.
Active-Passive Setup
In an active-passive setup, only one gateway is active at a time, while the other gateways remain passive and take over only if the active gateway fails. This configuration is simpler and more cost-effective, providing efficient failover. However, it has limited scalability and may underutilize resources in passive nodes.
Recommended Solution
The choice between active-active and active-passive setups depends on the customer’s requirements. For high availability and fault tolerance, active-active is recommended. For cost-effectiveness and simplicity, active-passive may be suitable.
Zone Redundancy for ExpressRoute
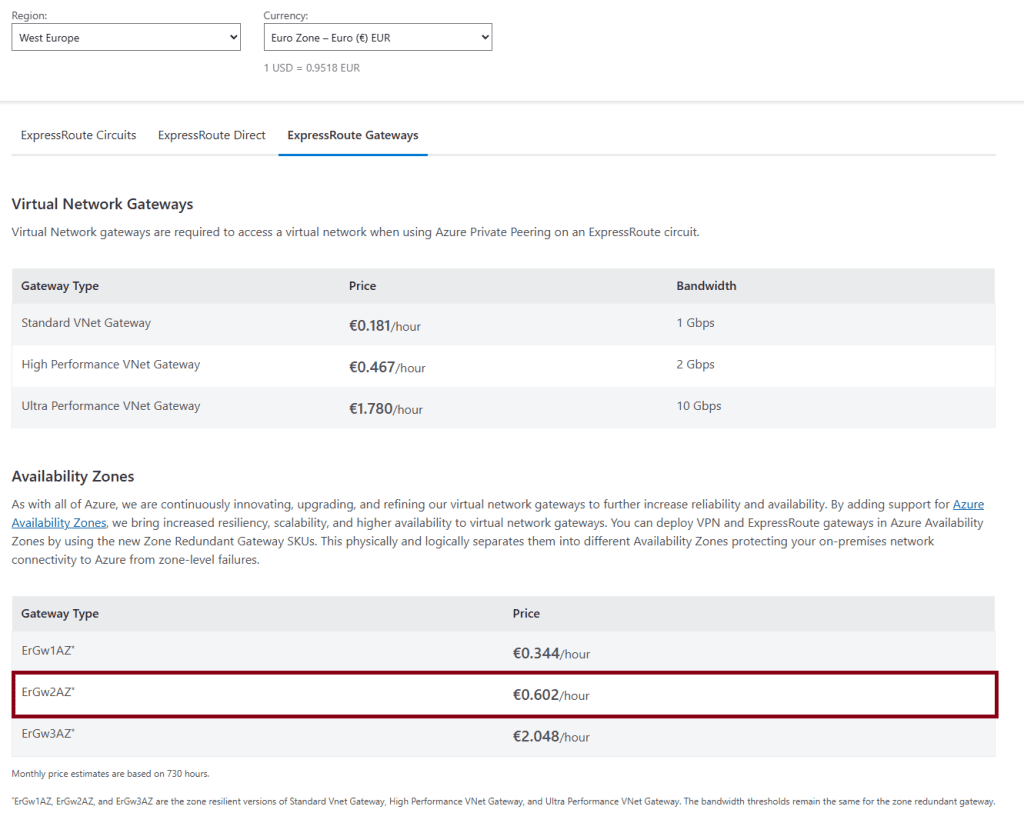
Zone redundancy distributes gateways across multiple fault zones, enhancing resiliency. This setup ensures that if one zone experiences issues, the other zones can maintain connectivity. Zone redundancy provides higher availability and fault tolerance by distributing resources across different physical locations within a region. In the West Europe region, an ExpressRoute gateway can be configured to run simultaneously in three zones. If one zone goes down, the other zones remain live, ensuring continuous connectivity. Upgrading to zone redundancy will affect pricing, as it incurs additional costs.
Identifying Affected Services
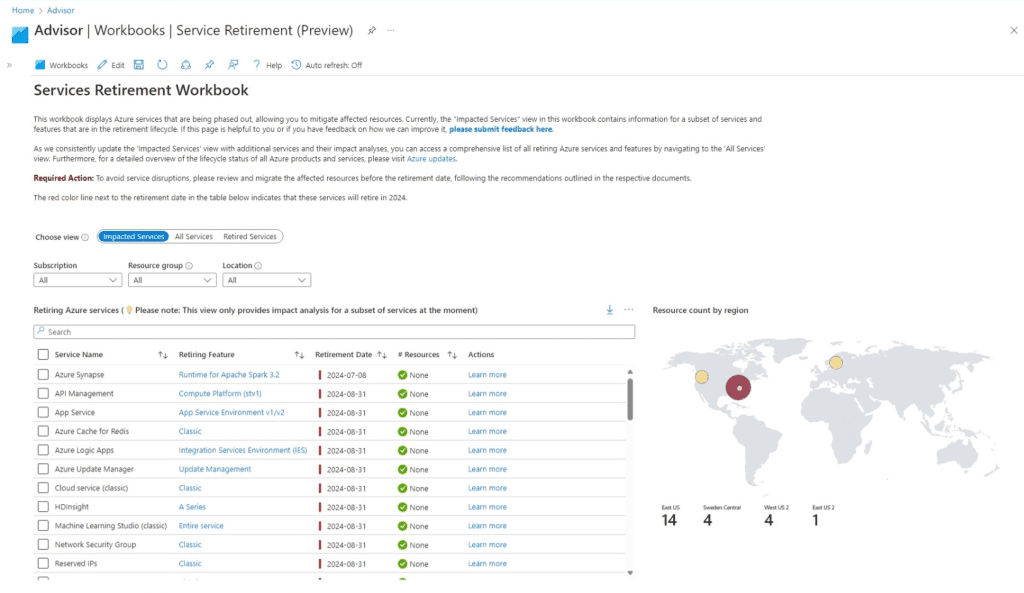
To determine if your services are impacted by the Basic SKU retirement, utilize the Services Retirement workbook within Azure Advisor. This tool provides insights into upcoming retirements and helps plan necessary migrations. The workbook highlights services using Basic SKU public IPs and offers recommendations for transitioning to Standard SKU.
Detailed Explanation of Basic SKU Retirement for Public IPs
The retirement of Basic SKU Public IPs requires customers to upgrade to Standard SKU. Many customers aim to avoid downtime during this transition. We will provide guidance on how to achieve this seamlessly. The Standard SKU offers enhanced features such as zone redundancy, improved security, and higher availability, making it a suitable replacement for the retiring Basic SKU.
ExpressRoute Gateway Upgrade Process
Upgrading the ExpressRoute gateway involves changing the SKU to zone redundant, which creates a new public IP and upgrades the gateway to a zone redundant setup. This new public IP will be distributed across multiple fault zones, ensuring higher availability and resiliency. This process requires reconfiguration of other points, including on-premises firewalls. Upgrading to a zone redundant ExpressRoute gateway is recommended for increased reliability, as zone redundancy means distributing gateways across multiple fault zones, enhancing resiliency.
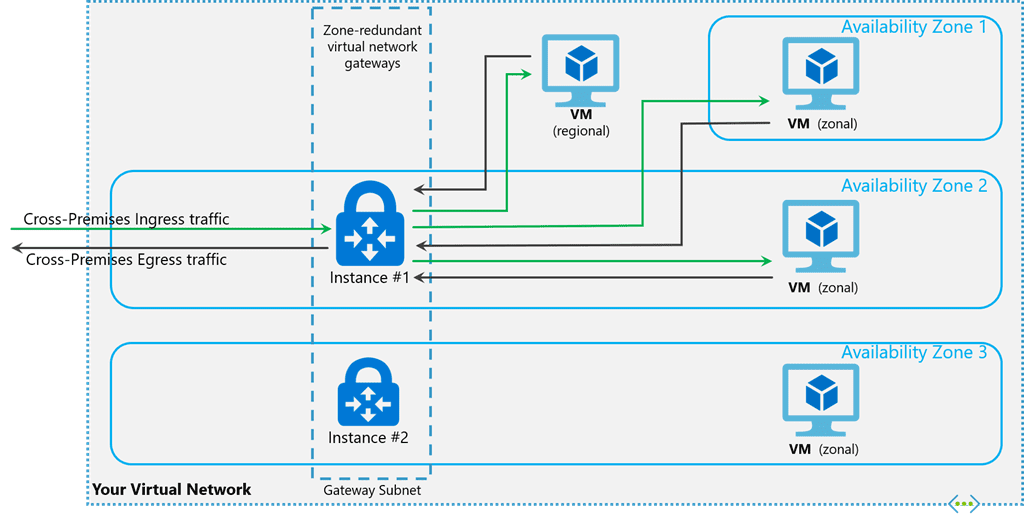
The infographic illustrates how zone-redundant virtual network gateways are deployed across different availability zones to ensure redundancy and reliability. Specifically, Instance #1 is located in Availability Zone 2, and Instance #2 is located in Availability Zone 3. This setup ensures that if one availability zone experiences issues, the other zone can maintain connectivity. By physically and logically separating the gateways into different availability zones, the network connectivity to Azure is protected from zone-level failures. This means that for fault tolerance across multiple regions, you would need to deploy the gateway in each desired region separately. If you want fault tolerance across two regions, you would have to deploy an ErGw2AZ gateway twice, once in each region. This setup enhances the overall reliability and fault tolerance of the network, ensuring continuous connectivity even if multiple zones experience issues.
Why We Use ErGW2AZ: In our example, we use the ErGw2AZ SKU because it is a common choice for many enterprises due to its balance of performance and cost. The ErGw2AZ SKU offers a higher capacity and bandwidth compared to the basic SKUs, making it suitable for enterprise-level applications. Specifically, the ErGw2AZ SKU supports up to 10 Gbps of bandwidth, providing ample throughput for demanding workloads.
To upgrade the ExpressRoute gateway to a zone redundant setup, you can use the Azure portal, PowerShell, or CLI. The official guidance suggests creating a new IP first, but it is possible to directly upgrade the existing ExpressRoute gateway. Here are the general steps for upgrading via the Azure portal:
- Navigate to the Azure Portal: Log in to the Azure portal and go to the “Virtual Network Gateways” section.
- Select the Existing Gateway: Choose the ExpressRoute gateway you want to upgrade.
- Upgrade the SKU: In the gateway settings, select the option to upgrade the SKU to a zone redundant setup. This will automatically create a new Standard SKU public IP and associate it with the gateway.
- Confirm the Upgrade: Review the changes and confirm the upgrade. The Azure portal will handle the creation of the new public IP and the upgrade process.
- Reconfigure On-Premises Firewalls: Update the on-premises firewall rules to allow traffic from the new public IP address.
- Verify Connectivity: Ensure that the new gateway is operational and that connectivity is maintained.
- Navigate to the Azure Portal: Log in to the Azure portal and go to the “Virtual Network Gateways” section.
- Select the Existing Gateway: Choose the ExpressRoute gateway you want to upgrade.
- Upgrade the SKU: In the gateway settings, select the option to upgrade the SKU to a zone redundant setup. This will automatically create a new Standard SKU public IP and associate it with the gateway.
- Confirm the Upgrade: Review the changes and confirm the upgrade. The Azure portal will handle the creation of the new public IP and the upgrade process.
- Reconfigure On-Premises Firewalls: Update the on-premises firewall rules to allow traffic from the new public IP address.
- Verify Connectivity: Ensure that the new gateway is operational and that connectivity is maintained.
VPN Gateway Upgrade Process
Upgrading a VPN gateway from Basic to Standard SKU requires deleting the current gateway and creating a new one. This process involves removing existing connections, creating a new gateway with a Standard SKU public IP, and re-establishing connections. Customers can schedule the upgrade during non-business hours to minimize the impact on operations. Additionally, pre-configuring the new gateway settings and testing the connectivity before the actual migration can help reduce downtime. Here are the required steps:
- Prepare for the Upgrade: Schedule a suitable maintenance window to minimize the impact on operations. Notify stakeholders of the planned downtime.
- Remove Existing Connections: In the Azure portal, go to the “Virtual Network Gateways” section and remove any existing connections to the VPN gateway.
- Delete the Current Gateway: Delete the existing VPN gateway. This will also remove the associated Basic SKU public IP.
- Create a New Gateway: Create a new VPN gateway with a Standard SKU public IP. Configure the gateway settings as needed.
- Update On-Premises VPN Devices: Update the on-premises VPN devices with the new VPN gateway IP address.
- Re-establish Connections: Recreate the connections to the virtual network gateway and verify connectivity.
- Test and Validate: Test the new VPN gateway to ensure that it is operational and that connectivity is maintained.
By following these steps, you can upgrade your VPN gateway to a Standard SKU public IP, ensuring enhanced reliability and minimal downtime during the transition.
Conclusion
In this article, we have explored the upcoming retirement of Basic SKU Public IPs and provided comprehensive guidance for Solution Architects and IT Managers to manage this transition effectively. We covered key concepts such as the differences between Basic and Standard SKUs, VPN and ExpressRoute gateways, and the importance of zone redundancy. We also discussed the implications of the Basic SKU retirement and provided step-by-step guidance for upgrading both ExpressRoute and VPN gateways. By understanding these concepts and following the recommended upgrade processes, you can ensure a seamless transition with minimal downtime and enhanced reliability for your network infrastructure.