Introduction
Azure ExpressRoute provides a faster, more reliable, and private connection between your on-premises infrastructure and Microsoft Azure. This guide aims to give you a comprehensive understanding of ExpressRoute, including its benefits, implementation process, and how it integrates with third-party firewalls like Palo Alto. We will also cover Transport Layer Security (TLS) inspection and termination, pricing considerations, and the role of edge sites in ExpressRoute connectivity.
Understanding Azure ExpressRoute
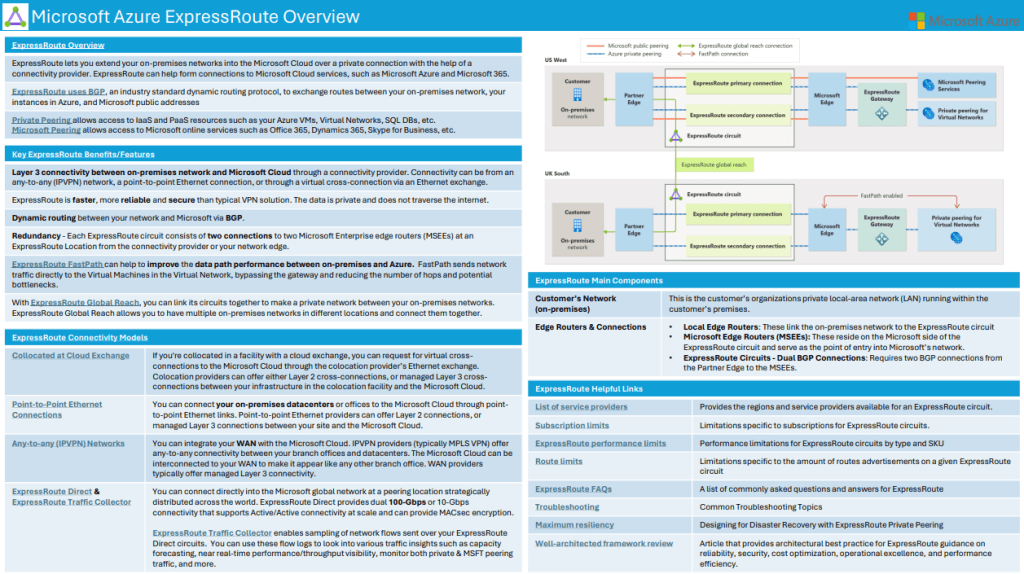
Azure ExpressRoute is a service that enables you to create private connections between Azure datacenters and infrastructure on your premises or in a colocation environment. These connections do not go over the public Internet, offering higher security, reliability, and speed.
Difference Between ExpressRoute and Regular Virtual Private Network (VPN) Gateways
ExpressRoute differs significantly from regular VPN (virtual private network) gateways, which utilize the public Internet for connectivity. VPN gateways encrypt data and send it over the public Internet, which can introduce latency and potential security vulnerabilities. ExpressRoute, on the other hand, uses private connections that do not traverse the public Internet, providing a higher level of security and more consistent network performance with lower latency.
Encryption Considerations
Encryption is generally not required for ExpressRoute because the connections are private and do not go over the public Internet. This inherent security reduces the need for encryption, which is essential for VPN tunnels that rely on public Internet pathways. However, if encryption is used, it can introduce overhead for compute resources on network virtual appliances (NVAs) such as firewalls, increasing latency and reducing performance.
TLS Inspection and Termination
TLS inspection and termination are critical for maintaining security. Typically, TLS termination happens at the firewall, either Azure Firewall Premium or third-party firewalls like Palo Alto, if they support TLS termination.
Palo Alto Firewalls and TLS Termination
When using Palo Alto firewalls with ExpressRoute, TLS termination can be efficiently managed. Palo Alto firewalls act as NVAs and are capable of performing TLS termination tasks. This involves decrypting the incoming encrypted traffic, inspecting it for any threats or anomalies, and then re-encrypting the traffic before forwarding it to its destination. This process ensures that the data remains secure while allowing for thorough inspection to detect and mitigate potential security threats.
To set up TLS termination on a Palo Alto firewall with ExpressRoute, the following steps are generally followed:
- Deploy the Palo Alto firewall as an NVA in your Azure environment.
- Configure the firewall to handle TLS termination by importing the necessary SSL certificates.
- Set up policies to dictate how the firewall should inspect and handle decrypted traffic.
- Ensure that the firewall is integrated into the ExpressRoute circuit to manage the traffic flow efficiently.
By leveraging Palo Alto firewalls for TLS termination, businesses can achieve a high level of security while maintaining the performance and reliability that ExpressRoute offers.
Benefits of ExpressRoute
- Increased Security: Since the connection does not traverse the public Internet, it offers greater security and reduces the risk of cyber threats.
- Enhanced Reliability: Provides more consistent network performance with lower latency.
- Higher Speed: Offers higher bandwidth options than typical Internet connections.
- Global Reach: Enables connectivity across multiple Azure regions.
- Redundancy: ExpressRoute circuits are designed to be highly available and reliable, with built-in redundancy to ensure continuous connectivity.
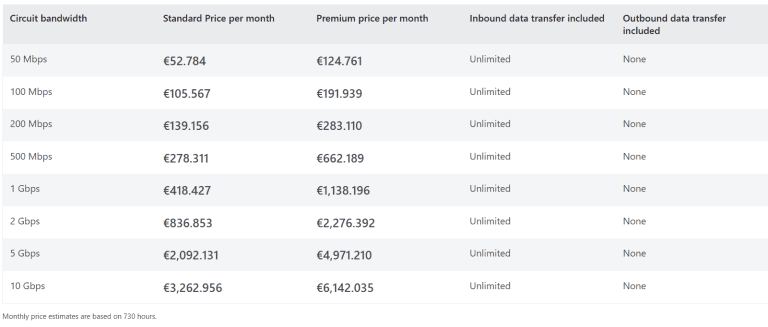
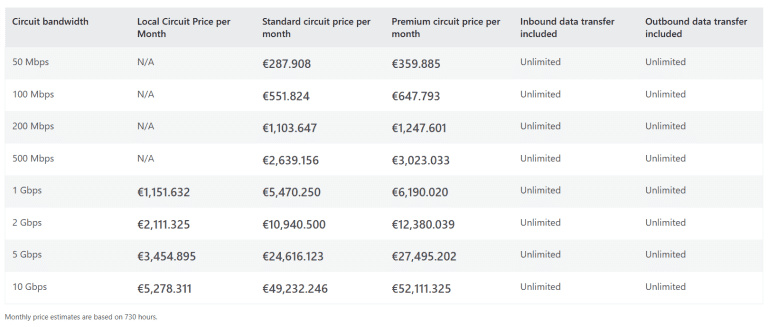
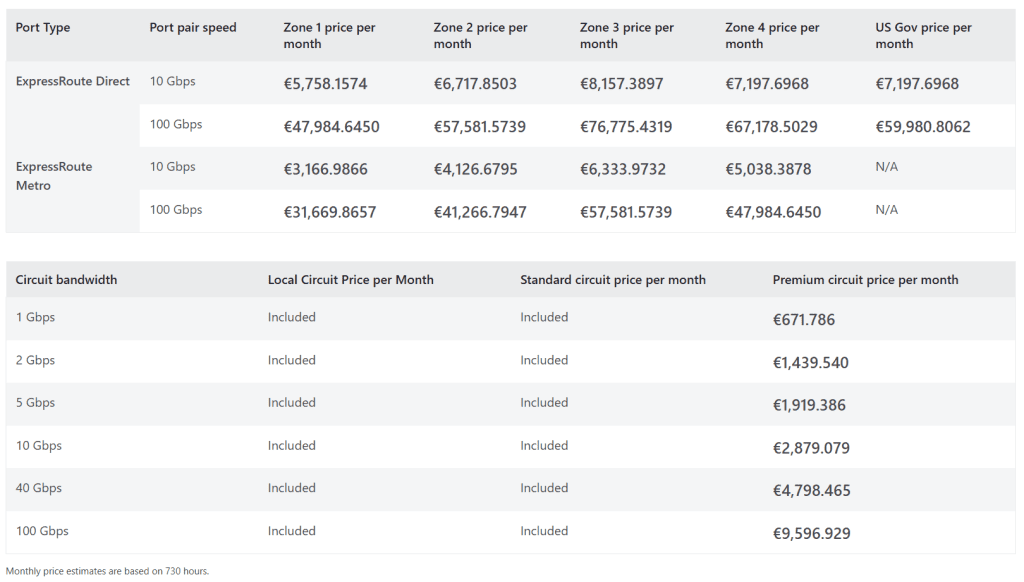
Available Tiers and Pricing of ExpressRoute
Azure ExpressRoute offers different tiers to fit various needs, each with its own pricing considerations:
- Local: Provides connectivity to Azure resources within the same metro area or city and its immediate surroundings. It is the most cost-effective option for localized operations. Example: Vienna and its surrounding areas in Austria.
- Standard: Allows connectivity to Azure regions within the same geopolitical area, such as a country or a group of closely tied countries, offering a balance of cost and coverage. Example: The European Union.
- Premium: Extends connectivity to Azure regions globally, enabling a truly global network footprint. It is the most expensive option but essential for businesses with global operations.
In addition to these tiers, Azure ExpressRoute offers two data plans:
- Metered Data Plan: Charges based on the amount of data transferred over the ExpressRoute circuit. This plan is suitable for businesses with variable data transfer needs.
- Unlimited Data Plan: Offers a fixed price for unlimited data transfer, making it ideal for businesses with high and consistent data transfer requirements.
ExpressRoute Direct
ExpressRoute Direct provides dedicated, high-capacity connections directly to Microsoft’s global network. This option is ideal for organizations that require higher bandwidth and enhanced security. With ExpressRoute Direct, you can connect directly to Microsoft at peering locations strategically placed around the world. This service offers dual 100 Gbps or 10 Gbps connectivity, ensuring high availability and redundancy. It is particularly beneficial for scenarios that demand large-scale data ingestion, such as data analytics, backup, and recovery operations.
Multi-Region Strategy and Pricing Considerations
Implementing a multi-region strategy involves having resources in at least two regions, such as West Europe and North Europe, or Austria and West Europe. This strategy ensures redundancy and disaster recovery.
Regional Pairs and Preferred Regions
Azure regions are often paired to ensure data residency and compliance. Peered regional pairs can be selected to optimize connectivity and performance. However, customers can also select preferred regions based on their specific needs, which can affect pricing.
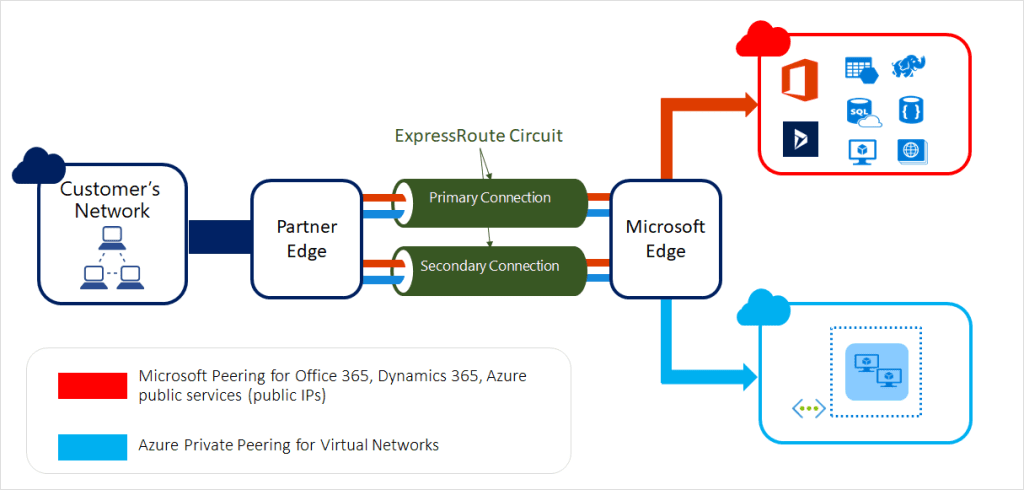
What is an Edge Site?
An edge site is a physical location where Microsoft’s network connects to your network through ExpressRoute. These sites are strategically placed to minimize latency and maximize performance, enabling efficient data transfer between your on-premises infrastructure and Azure. For example, in Austria, a possible edge site could be in Vienna, where Microsoft has partnered with local data centers to provide ExpressRoute connectivity.
Microsoft Edge vs. Partner Edge Sites
Understanding the difference between Microsoft Edge and Partner Edge sites is crucial for managing responsibilities and expectations:
- Microsoft Edge Sites: These are directly managed by Microsoft and are part of Microsoft’s global network infrastructure. They ensure high-performance connectivity and are integrated into Microsoft’s network backbone. The responsibility for managing and maintaining these sites lies with Microsoft, providing a seamless experience for customers.
- Partner Edge Sites: These are managed by third-party connectivity providers who have partnered with Microsoft to extend ExpressRoute connectivity. These providers facilitate the physical connection to the edge site and may offer additional services such as managed connectivity solutions. The responsibility for managing and maintaining these sites lies with the partner, and customers need to coordinate with the provider for any support or maintenance issues.
Implementation of ExpressRoute
Implementing Azure ExpressRoute involves a series of steps to establish a secure and reliable connection between your on-premises infrastructure and Microsoft Azure. This section will guide you through the entire process, from provisioning the ExpressRoute circuit to connecting your on-premises network and managing traffic within Azure. By following these steps, you can ensure a seamless and efficient implementation of ExpressRoute for your organization.
End-to-End Process
- Provisioning: Set up an ExpressRoute circuit through the Azure portal or PowerShell.
- Connecting On-Premises to Azure: Use a connectivity provider to link your on-premises network to an edge site. The role of third parties is crucial here, as they facilitate the physical connection to the edge site.
- Traffic Transfer within Azure: Traffic between Azure regions is handled through Microsoft’s private global network, ensuring high performance and reliability.
To look up corresponding partners to establish an ExpressRoute connection, customers can visit the Azure ExpressRoute partners page. This page provides a list of connectivity providers and locations where ExpressRoute is available.
Initiating the Process
The process of setting up ExpressRoute is typically initiated by the customer. However, it can also be facilitated by a third party on behalf of the customer. Microsoft provides the infrastructure and support needed for the setup.
Integrating with Third-Party Firewalls
ExpressRoute can be integrated with third-party firewalls like Palo Alto. These firewalls act as Network Virtual Appliances (NVAs) and can handle various security tasks, including TLS inspection and termination.
Conclusion
Azure ExpressRoute offers a robust, secure, and highly reliable way to connect your on-premises infrastructure with Microsoft Azure. By understanding the benefits, tiers, and implementation process, as well as how to integrate third-party firewalls and consider multi-region strategies, you can make informed decisions about leveraging ExpressRoute for your business.