Introduction
In today’s rapidly evolving technological landscape, enterprises are increasingly moving towards cloud-based solutions to improve agility, scalability, and cost-efficiency. Azure, Microsoft’s cloud platform, offers a robust framework for managing resources through various subscription models. For central IT teams serving multiple business units, balancing unmanaged vs managed environments becomes a critical task. This article provides guidance on managing these environments, transitioning towards a product-centric culture, and maintaining essential control over vital components.
The CAF Landing Zone Concept
The Cloud Adoption Framework (CAF) for Azure helps organizations align their cloud strategy with business objectives. Having already implemented the CAF landing zone concept, your central team must navigate the responsibilities associated with platform and landing zone subscriptions. Let us explore the differences between unmanaged and managed environments and the necessity of transitioning towards a product-centric culture.
Unmanaged Environments
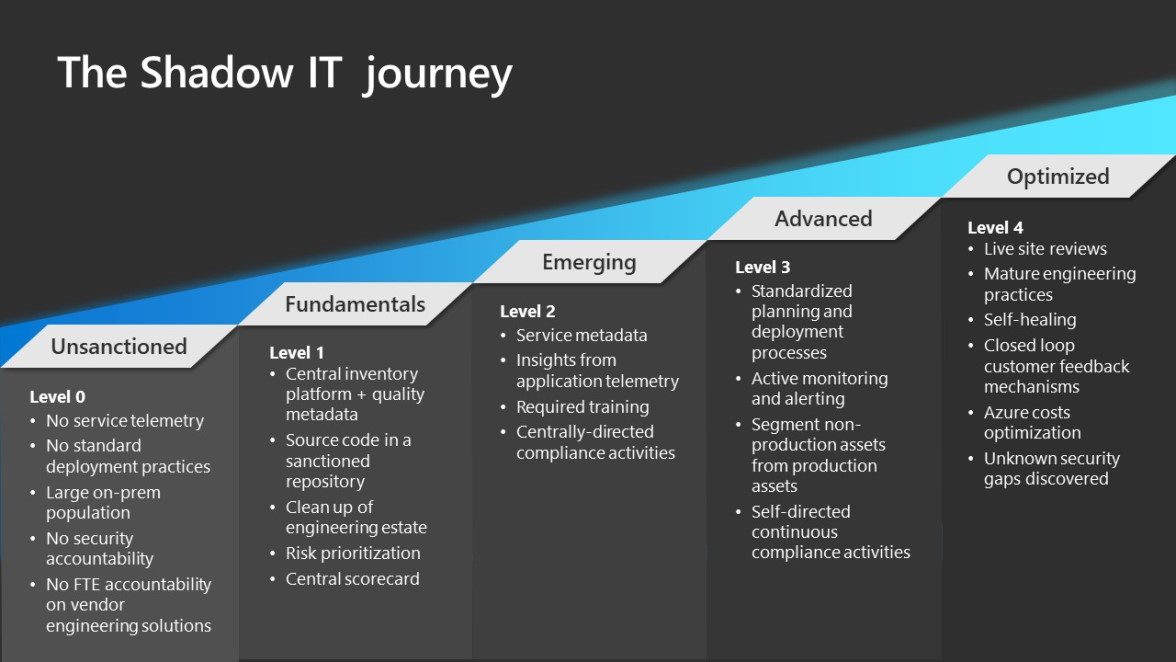
In unmanaged environments, business units or product teams have full responsibility for their subscriptions. This model, akin to sandbox subscriptions, empowers teams to innovate rapidly without waiting for central approvals. However, it comes with risks, such as inconsistency in security practices, potential misconfigurations, and lack of governance. Without central oversight, these environments can lead to shadow IT, where teams deploy resources without adhering to organizational standards, ultimately risking security and compliance.
Shadow IT can introduce vulnerabilities that may be exploited by malicious actors, leading to data breaches and loss of sensitive information. Additionally, the lack of a unified approach to resource management can result in inefficient use of cloud resources, causing unnecessary expenses. Therefore, while unmanaged environments offer flexibility, they must be handled with caution to mitigate potential risks.
Managed Environments
Conversely, managed environments see the central IT team fully responsible for the configuration, maintenance, and security of the subscriptions. This model ensures adherence to organizational policies and standards but can stifle innovation due to bureaucratic processes. The central IT team acts as a gatekeeper, potentially causing delays in deployment and limiting the agility of product teams. While this model provides strong control, it may create bottlenecks that hinder responsiveness to market demands.
However, managed environments have the advantage of providing a consistent and secure framework for resource management. By centralizing control, organizations can enforce standard practices across all teams, ensuring compliance with regulatory requirements and internal policies. Managed environments also facilitate better resource utilization and cost management, as the central IT team can monitor and optimize cloud usage across the enterprise.
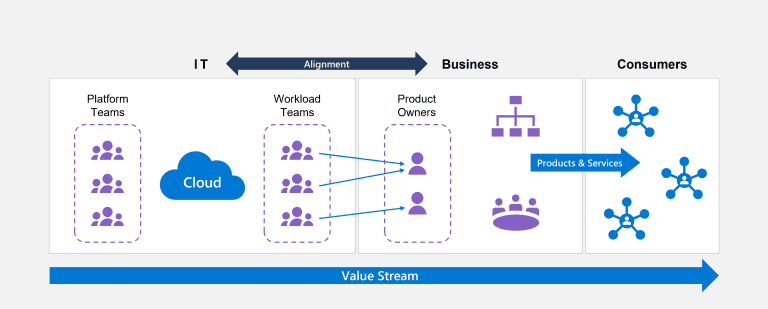
Transitioning to a Product-Centric Culture
The classical siloed approach, where central IT teams manage everything, is increasingly seen as inefficient. The CAF recommends delegating responsibilities to product teams, fostering a product-centric culture. Here’s why this transition is necessary:
Agility and Innovation
Product teams are closer to the end-users and understand their needs better. By granting them more control, they can rapidly innovate and respond to market changes, leading to improved products and services. This agility allows organizations to stay competitive and meet customer demands more effectively.
With greater autonomy, product teams can experiment with new technologies and methodologies, fostering a culture of continuous improvement. This innovation is crucial in a dynamic market where customer preferences and technological advancements evolve rapidly. By empowering product teams, organizations can reduce time-to-market and enhance their ability to adapt to changing conditions.
Empowering Product Teams for Agile Innovation
Ownership and Accountability
When product teams are responsible for their environments, they develop a sense of ownership and accountability. This leads to better decision-making and adherence to best practices. Teams that own their processes and outcomes are more likely to invest in continuous improvement and quality assurance.
Ownership also promotes a proactive approach to problem-solving. Product teams, being directly accountable for their solutions, are more invested in identifying and addressing issues promptly. This reduces the likelihood of recurring problems and enhances the overall reliability and performance of the solutions.
Empowerment in Action: A Product Team’s Commitment to Excellence
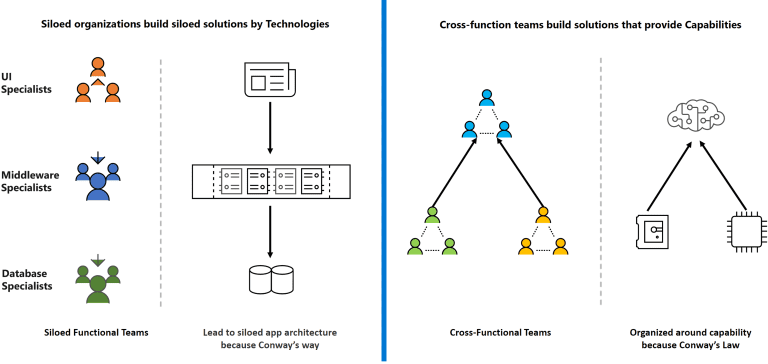
Reverse Conway’s Law
Conway’s Law states that organizations design systems that mirror their communication structures. The reverse implies that to achieve desired system architectures, organizations must structure their teams accordingly. By adopting a product-centric culture, enterprises can align their team structures with their architectural goals, promoting better collaboration and more efficient workflows.
Aligning team structures with system architectures fosters seamless communication and collaboration. This alignment ensures that teams work towards common objectives, reducing misunderstandings and conflicts. It also enables organizations to leverage the collective expertise of their teams, leading to more robust and innovative solutions.
Components Under Central IT Responsibility
While transitioning responsibilities, it is crucial to maintain central oversight over certain components to ensure consistency and security across the enterprise. These include:
- Networking: Initial network configurations, such as Virtual Networks (VNets), subnets, and VPN Gateways, should be set up by the central IT team to ensure secure and efficient connectivity. Proper network setup is foundational to maintaining security and operational efficiency across all environments.
- DNS Configuration: Centralizing Domain Name System (DNS) management helps maintain an organized and conflict-free naming structure across the enterprise. This prevents naming conflicts and ensures that all resources can be accessed efficiently.
- Security: Core security measures, such as Identity and Access Management (IAM), should be managed centrally to enforce stringent security protocols. This includes implementing multi-factor authentication (MFA), regular security assessments, and compliance with industry standards.
- Azure Policies: Azure Policies are essential for enforcing organizational standards. Centrally managed policies can prevent unwanted actions, such as the creation of public IP addresses or modifications to critical resources. Policies can also ensure compliance with regulatory requirements and internal guidelines.
- Management Groups: Management Groups in Azure allow you to manage access, policies, and compliance for multiple subscriptions. Central IT should configure these groups to ensure a structured hierarchy and consistent policy application. This helps in maintaining a unified governance framework across the organization.
Additionally, central IT can provide “trusted” repositories containing components approved by central IT and aligned with internal standards and policies. Product teams should have the option to contribute towards this “product catalogue” or repository, ensuring that the repository evolves with the organization’s needs while maintaining compliance and security standards. This collaborative approach allows product teams to leverage centrally approved components while contributing to the repository’s growth and relevance.
Aligning with RBAC, PIM, and RACI
To successfully manage these responsibilities, it is essential to align with the following concepts:
Role-Based Access Control (RBAC)
RBAC allows you to assign specific permissions to users based on their role within the organization. This ensures that only authorized individuals can perform certain actions, minimizing the risk of errors and security breaches. By clearly defining roles, organizations can ensure that users have the appropriate level of access needed to perform their duties.
RBAC provides a structured approach to access management, allowing organizations to implement the principle of least privilege. By granting users only the permissions necessary for their roles, organizations can reduce the attack surface and minimize the potential impact of security incidents. Regular reviews of RBAC assignments are essential to ensure that permissions remain appropriate and reflect changes in roles and responsibilities.
Custom RBAC Roles
Custom Role-Based Access Control (RBAC) roles are essential in managing Azure environments effectively. These roles allow for precise control over user permissions, preventing unauthorized deployments and configurations, such as VPN gateways or firewalls. Custom RBAC roles, tailored to the specific needs of an organization, can limit actions to ensure compliance with security policies and operational standards. In addition to using custom roles, deny assignments can be attached to specific roles to further restrict actions that could lead to potential security risks or operational issues.
Implementing custom RBAC roles involves defining specific permissions that align with the organization’s security and operational requirements. These roles can be granular, allowing for detailed control over who can create, modify, or delete resources. By implementing custom RBAC roles, organizations can empower product teams to operate autonomously while maintaining control over critical actions that could impact security or compliance.
Moreover, deny assignments provide an additional layer of security by explicitly preventing specific actions, even if a user has other permissions that would normally allow those actions. This ensures that critical security and compliance requirements are enforced consistently across the organization.
Privileged Identity Management (PIM)
PIM enhances security by enabling just-in-time privileged access and enforcing policies for elevated roles. Central IT should use PIM to manage high-risk privileges. PIM ensures that elevated access is granted only when necessary and is subject to rigorous auditing and approval processes.
PIM provides an additional layer of security by managing and monitoring the use of privileged accounts. By implementing PIM, organizations can reduce the risk of misuse or compromise of privileged accounts, which are often targeted by attackers. PIM also enables organizations to enforce time-bound access, ensuring that elevated privileges are granted only for the duration needed to perform specific tasks.
RACI Model
The RACI (Responsible, Accountable, Consulted, and Informed) model helps define roles and responsibilities within the team structure. Here’s a suggested RACI matrix for managing Azure environments:
Task | Responsible | Accountable | Consulted | Informed |
Managing VNets | Central IT | Central IT | Security Team | Business Stakeholders |
Developing New Features | Product Teams | Product Teams | Central IT | Business Stakeholders |
Implementing Security Protocols | Central IT | Central IT | Security Team | Product Teams |
Deploying Applications | Product Teams | Product Teams | Central IT | Business Stakeholders |
Monitoring Compliance | Central IT | Central IT | Security Team | Product Teams |
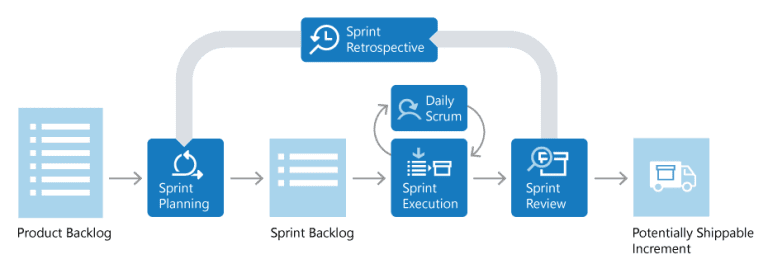
The Benefits of Agile Product Development
Transitioning to an agile product development cycle, rather than a traditional waterfall model, is essential for modern enterprises. Delivering small, workable products—known as Minimum Viable Products (MVP)—is more beneficial than the traditional approach. Here’s why:
- Rapid Feedback: MVPs allow product teams to receive immediate feedback from users, enabling continuous improvement and alignment with customer needs.
- Incremental Improvement: By delivering features incrementally, teams can adapt to changes and add additional functionalities as required or demanded by customers, avoiding overengineering and ensuring that resources are focused on adding value.
- Reduced Risk: Smaller releases reduce the risk of project failure. Issues can be identified and addressed promptly, minimizing the impact on the overall product.
- Flexibility: Agile development promotes flexibility and responsiveness to market demands. It allows teams to pivot and make necessary adjustments without the constraints of a rigid plan.
Agile development methodologies, such as Scrum and Kanban, provide structured frameworks for iterative and incremental development. By adopting these methodologies, organizations can improve collaboration, enhance transparency, and increase the predictability of project outcomes. Agile practices also emphasize regular retrospectives, enabling teams to reflect on their performance, identify areas for improvement, and implement changes to enhance efficiency and effectiveness.
The Cloud Operating Model vs. Cloud Operations Model
Understanding the distinction between the Cloud Operating Model and the Cloud Operations Model is crucial for effective management. The Cloud Operating Model focuses on the strategic alignment of cloud initiatives with business objectives, fostering innovation and agility. It encompasses governance, policy management, and organizational structure. The Cloud Operations Model, on the other hand, deals with the day-to-day management of cloud resources, including monitoring, maintenance, and incident response. Both models are interdependent and must be harmonized to achieve optimal performance and governance.
The Cloud Operating Model emphasizes the importance of aligning cloud initiatives with business goals. It involves setting strategic objectives, defining governance frameworks, and establishing policies that guide cloud adoption and usage. This model ensures that cloud investments deliver value to the organization and support its long-term objectives. The Cloud Operations Model, meanwhile, focuses on the practical aspects of managing cloud resources. It involves implementing monitoring tools, automating maintenance tasks, and responding to incidents to ensure the reliability and performance of cloud services.
Effective cloud management requires a holistic approach that integrates both the Cloud Operating Model and the Cloud Operations Model. By aligning strategic objectives with operational practices, organizations can create a cohesive framework that supports innovation, enhances security, and optimizes resource utilization. This integrated approach enables organizations to leverage the full potential of cloud technologies while maintaining control and ensuring compliance.
Conclusion
In summary, a shift towards a product-centric culture in Azure management fosters greater innovation, ownership, and accountability. While the central IT team retains control over essential components such as networking and security, product teams can leverage this autonomy to drive rapid development and respond to market demands. By using RBAC, PIM, and the RACI model, organizations can create a balanced approach that aligns with business objectives and ensures operational efficiency. Addressing the limitations and challenges proactively will enable enterprises to maximize the benefits of this new approach.
Limitations and Future Research
While this approach offers numerous benefits, it is not without limitations. Potential challenges include:
- Resistance to change from teams accustomed to the classical model.
- Ensuring adequate training and support for product teams to manage their environments effectively.
- Balancing the need for innovation with the necessity of maintaining stringent security and compliance standards.
Future research should focus on measuring the long-term benefits of a product-centric approach, analyzing the impact on organizational agility, and identifying best practices for training and support. By addressing these challenges proactively, organizations can maximize the benefits of a product-centric approach while minimizing potential risks.