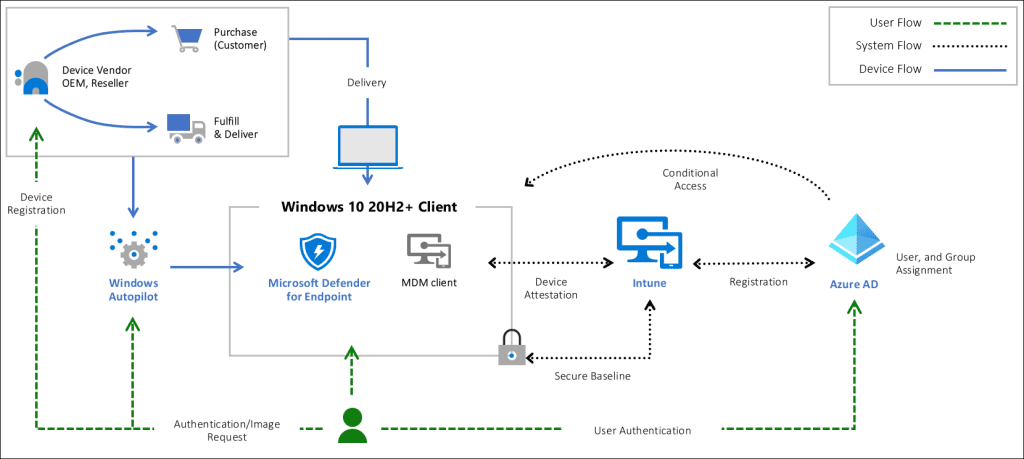
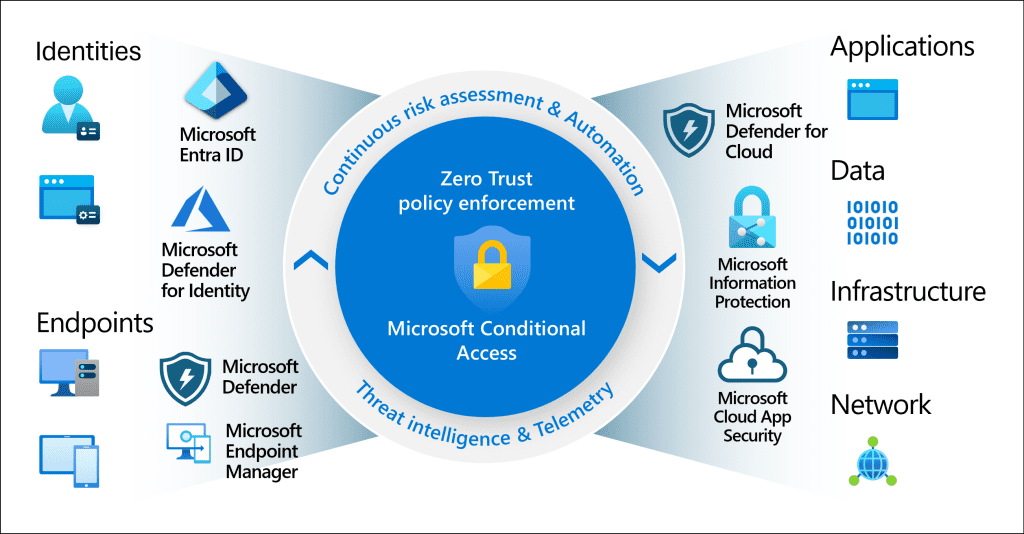
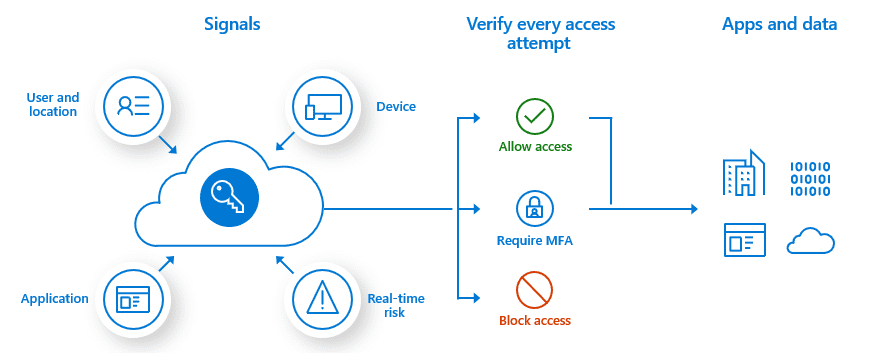
Introduction
In today’s rapidly evolving digital landscape, secure access management has become a paramount concern for organizations worldwide. The shift from the legacy Active Directory (AD) tier model to a modern enterprise access model presents a critical issue that many enterprises are grappling with. This transition is not merely a technological upgrade; it encompasses significant security, compliance, and operational challenges that must be addressed to safeguard sensitive data and maintain regulatory compliance. This article aims to shed light on these challenges and provide practical insights and solutions to facilitate a smooth transition.
Legacy AD Tier Model
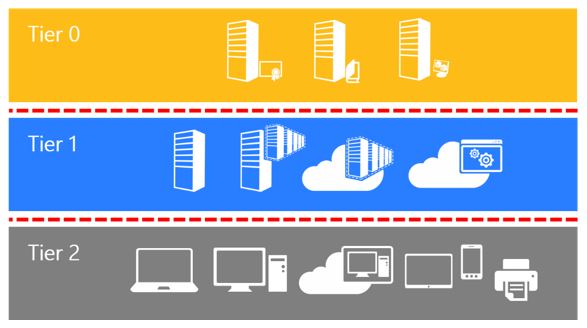
The legacy AD tier model has been a foundational component of enterprise security for many years. It is structured into three primary tiers:
- Tier 0: Domain Controllers and critical infrastructure. This tier includes the most sensitive components of the network, such as the AD database and other critical systems.
- Tier 1: Servers and applications. This tier encompasses the servers and applications that support the organization’s operations.
- Tier 2: Workstations and user devices. This tier includes the devices used by end-users to access network resources.
While this model has provided a robust framework for managing access, it also has its limitations. The rigid structure can lead to inefficiencies and create barriers to scalability and flexibility.
Challenges of the Legacy Model
One of the primary problems faced by organizations is the presence of admin users who lack a proper license and do not have a mailbox attached. This issue leads to a multitude of problems, including:
- Lack of notifications and alerts: Without a mailbox, admin users are unable to receive critical updates and alerts, which can hinder their ability to respond promptly to security incidents and operational issues.
- Compliance and auditing challenges: The absence of proper licensing and notification mechanisms complicates compliance with regulatory requirements and hampers effective auditing processes.
- Security risks: Unlicensed admin users pose significant security risks, including potential breaches, as their activities may go unmonitored and unreported.
- Reputational damage: Any breach or compliance failure can lead to reputational damage, resulting in a loss of customer trust and confidence.
- Legal consequences: Organizations may face legal repercussions, including fines under regulations such as NIS2, if they fail to address these security and compliance gaps.
Enterprise Access Model
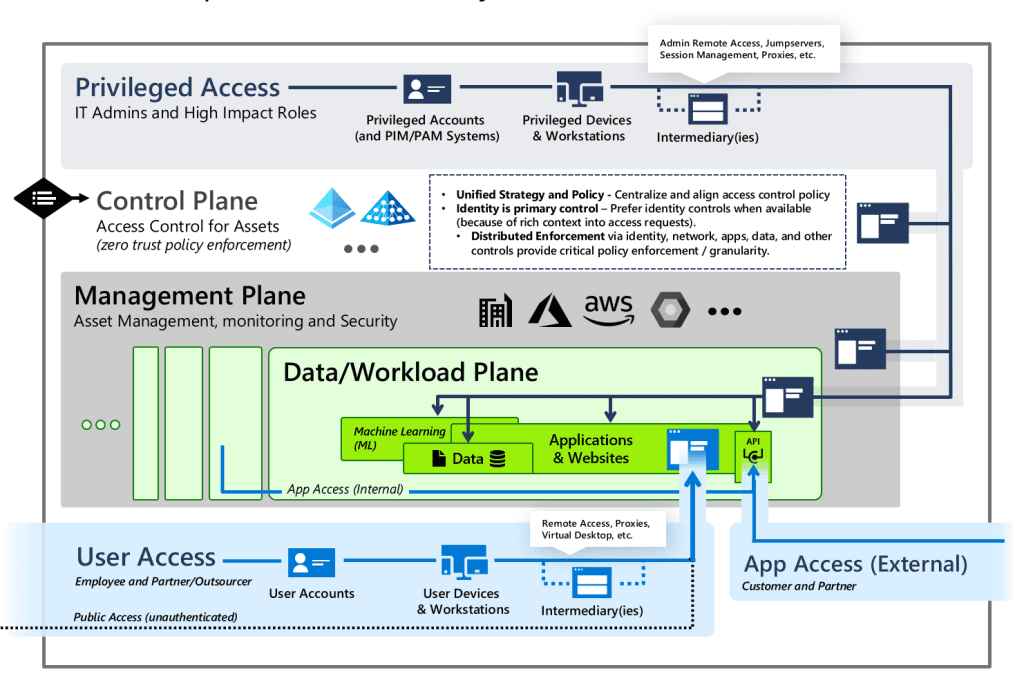
The modern enterprise access model represents a shift towards a more dynamic and adaptable approach to access management. It includes several key components:
- Privileged Access: This includes high-impact roles with access to sensitive systems. Effective management of privileged access is crucial to prevent unauthorized access and potential breaches.
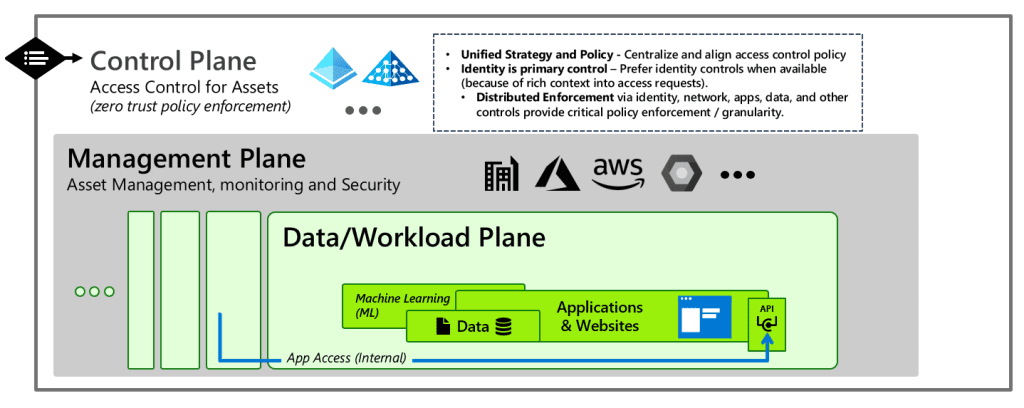
- Control Plane: This encompasses identity, policy enforcement, and security. It is responsible for ensuring that access policies are consistently applied and enforced across the organization.
- Management Plane: This involves asset management and monitoring. Effective management of IT assets and continuous monitoring are essential for maintaining security and compliance.
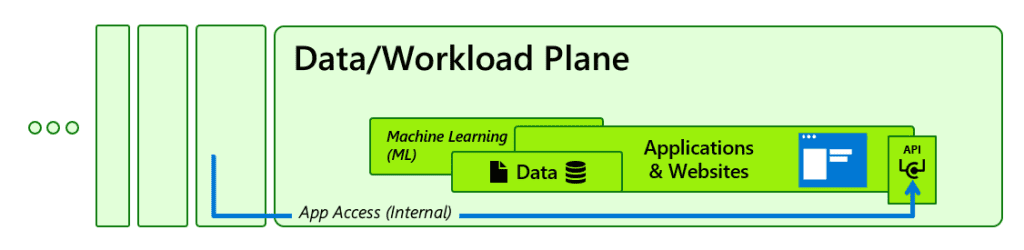
- Data/Workload Plane: This includes data storage and applications. Protecting sensitive data and ensuring the security of applications is a core aspect of the modern access model.
- User Access: This involves user accounts and devices accessing resources. Ensuring secure and efficient user access is critical for operational effectiveness.
The benefits of this model are numerous. It provides greater flexibility, scalability, and more robust security. By adopting this model, organizations can better manage access, enforce policies consistently, and protect sensitive assets more effectively.
Application Security
Managing application security without administrative privileges is paramount. Addressing potential risks involves thoroughly handling and checking privileges, access, APIs, and functions to prevent compromising Azure and other systems. Ensuring that applications follow the principle of least privilege can mitigate the risk of unauthorized access and prevent potential breaches.
Separation of Duties
Separation of duties is a critical aspect of access management. For example, having backup and restore privileges essentially makes someone an “Admin.” Clear role definitions and access controls are essential to prevent any single user from having excessive privileges. By separating duties, organizations can avoid conflicts of interest and reduce the risk of fraud and errors.
Just-in-Time Access
Just-in-Time (JIT) access is a concept where administrative privileges are granted only when needed and for a limited time. This approach minimizes the risk of unauthorized access and enhances security. By implementing JIT access, organizations can ensure that privileges are used only when necessary, reducing the window of opportunity for potential attacks.
Privileged Access Workstations (PAWs)
Privileged Access Workstations (PAWs) are dedicated workstations designed specifically for high-risk tasks that require elevated privileges. These workstations are configured with heightened security measures to mitigate risks associated with privileged access. PAWs differ from regular workstations in that they are used exclusively for administrative tasks and are often isolated from the general network to prevent cross-contamination. This isolation helps in protecting critical systems and data from potential threats that may arise from compromised user workstations.
Return on Security Investment (ROSI)
Understanding the concept of Return on Security Investment (ROSI) is crucial when transitioning to the modern enterprise access model. While businesses often focus on the financial cost of implementing security solutions, they frequently overlook the substantial impact of reputational loss and legal fines. Investing in robust security measures not only protects sensitive data but also enhances customer trust and compliance with regulatory standards. The long-term benefits of a secure infrastructure far outweigh the initial costs, making it a sound investment for any organization.
Licensing and User Recommendations
Transitioning to the modern enterprise access model requires careful consideration of licensing and user management. Organizations typically need to separate identities for control and management planes, which necessitates additional licensing. It is recommended to have at least two types of users:
- Standard users for regular tasks and access to everyday applications.
- Admin users with access restricted to privileged tasks and systems.
The number of licenses required will vary depending on the organization’s size and structure. It is crucial to conduct a thorough assessment to determine the exact licensing needs and ensure compliance with licensing agreements. Organizations should consider licenses that offer comprehensive security features and support a hybrid environment.
Privileged Identity Management (PIM) and Privileged Access Management (PAM)
Privileged Identity Management (PIM) and Privileged Access Management (PAM) are essential components of the enterprise access model. PIM focuses on managing and monitoring access to critical resources, ensuring that only authorized users have access to sensitive systems. PAM, on the other hand, involves overseeing the lifecycle of privileged accounts, from creation to deactivation. Both PIM and PAM align with the enterprise access model by providing a structured approach to managing and securing privileged access, thereby reducing the risk of unauthorized access and potential breaches.
Applicability to Cloud and Hybrid Environments
The modern enterprise access model is designed to be versatile and applicable to a variety of environments, including cloud, on-premises, and hybrid setups. The model supports integration with major public clouds such as Azure and AWS. This flexibility ensures that organizations can implement the model across different environments, maintaining consistent security and access management practices irrespective of where their resources are hosted.
Single User with Role Elevation
Some organizations may opt for an approach where a single user can elevate their role to a global administrator via Privileged Identity Management (PIM) to save on licensing costs. This approach has both benefits and drawbacks:
Benefits:
- Cost Savings: By reducing the number of privileged accounts, organizations can significantly cut down on licensing expenses.
- Simplified Management: Fewer accounts mean easier management and monitoring of user activities.
Drawbacks:
- Increased Risk: Having a single point of privilege escalation can create a vulnerability, as the compromise of this account could lead to significant security breaches.
- Operational Delays: The need to manually elevate privileges could introduce delays in responding to urgent security incidents or operational tasks.
- Compliance Issues: Regulatory requirements may mandate separation of duties, which is harder to achieve with a single user performing multiple roles.
To mitigate the increased risk, organizations can implement a four-eyes principle, where another admin must approve the role elevation via PIM before it occurs. This additional layer of verification ensures that no single user can unilaterally escalate their privileges, thereby reducing the risk of unauthorized access and potential breaches.
Conditional Access and Multi-Factor Authentication (MFA)
Conditional Access and Multi-Factor Authentication (MFA) are critical components of a secure access management strategy. Conditional Access policies allow organizations to control access based on specific conditions, such as user location, IP address, or device compliance status. For example, an organization can limit role elevation to specific IP addresses or locations, enhancing security for single user scenarios.
MFA is strongly recommended for all access scenarios as it provides an additional layer of security. Most breaches occur due to the lack of a second factor of authentication. MFA ensures that even if user credentials are compromised, unauthorized access is significantly more difficult. Organizations can choose from various MFA options, including:
- Microsoft Authenticator: A mobile app that provides a secure and convenient way to verify user identity.
- Biometric FIDO2 Key: A physical device that uses biometric data for authentication.
- Passkey: A passwordless authentication method that enhances security and user experience.
- Windows Hello: A biometric authentication feature built into Windows 10 and later versions, allowing users to sign in with their face, fingerprint, or PIN.
Implementing Conditional Access and MFA not only strengthens security but also aligns with regulatory compliance requirements and best practices for access management.
Limitations
It is important to acknowledge the limitations of both the legacy and modern models. The legacy model, while robust, lacks the flexibility and scalability needed to meet the demands of modern enterprises. On the other hand, the modern model, despite its advantages, requires careful planning and significant investment in terms of licensing and security infrastructure.
Conclusion
In conclusion, the transition from the legacy AD tier model to the modern enterprise access model is a critical step for organizations aiming to enhance their security posture and ensure compliance with regulatory requirements. By understanding the key differences and implications of these models, organizations can make informed decisions and implement effective strategies to manage access more securely and efficiently.
We strongly encourage organizations to review their current access management practices and align them with Microsoft’s recommendations for secure access management. By doing so, they can mitigate risks, ensure compliance, and protect their valuable assets in today’s complex digital landscape. This transition is not without its challenges, but with the right approach and commitment, it can lead to significant improvements in security and operational efficiency.